3D printers will become attractive targets for cyberattacks because 3D-printed objects and parts are finding more and more use in critical infrastructures around the world, such as in healthcare, transportation, robotics, aviation, and space, researchers say.
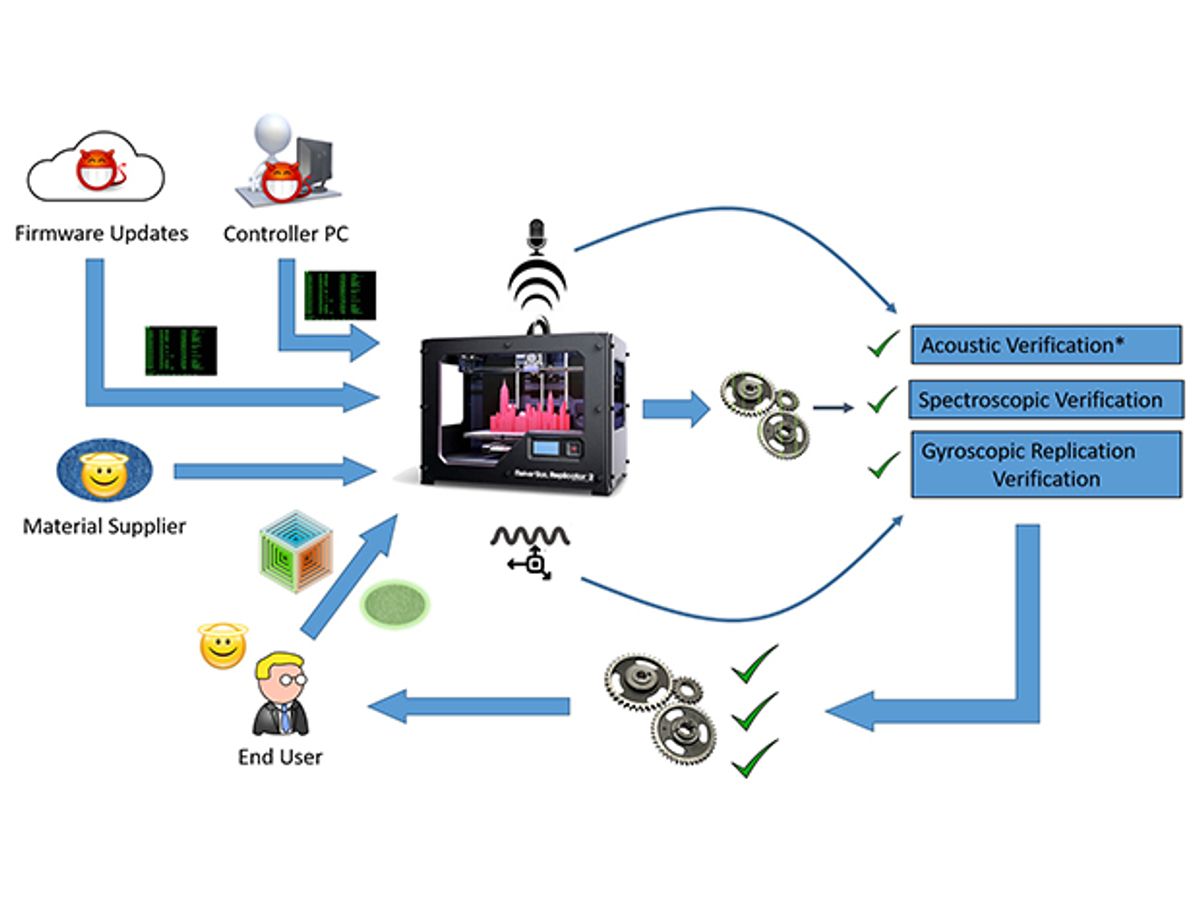
In response to the threat, a trio of techniques to monitor 3D printers for cyberattacks is revealed in a new study from researchers at Rutgers University and the Georgia Institute of Technology.
3D-printing is increasingly playing a part in situations where lives may be at stake, medical prostheses or car parts, for example. However, there is currently no standard way to verify that the 3D-printed parts were made accurately, the researchers say.
“3D printing will be used for manufacturing almost everything: artificial organs, homes, buildings, and even aircraft parts,” says study co-author Mehdi Javanmard, an electrical engineer at Rutgers University in New Jersey. “With wireless connectivity of controllers, unknown and undetectable cyber-physical attacks can result in devastating effects without any way to trace the attacks.”
Previous work suggested that hackers targeting 3D printers could easily leave defects within 3D-printed objects that were imperceptible from the outside and reduced the amount of stress the items could withstand by 14 percent. Other researchers have shown in a YouTube video that hacking a 3D printer could lead to a defective propeller in a drone, causing it to crash.
The researchers focused on three different ways to determine if a 3D printer was hacked. One method involved monitoring the 3D motions of the extruder, the arm through which materials are printed to form objects. This method used a gyroscope and other sensors attached to the extruder.
Another technique used microphones to monitor the sounds that the 3D printer made as it worked. Essentially, it treated all the sounds the device generated as a song and listened for any off or missing notes.
The final method examined a completed object to see if it was printed correctly. Gold nanoparticles or stainless steel filaments were embedded within the printed material, which helped laser or X-ray scans identify defects within the printed items. These are “the same kinds of techniques used in medical imaging for detection of tumors,” Javanmard says.
In experiments with three different types of 3D printers and one computer-numerically-controlled (CNC) machining device, all three hacking-detection methods were 100 percent accurate at detecting misprints in real time.
The scientists detailed their findings on 16 August at the USENIX Security Symposium in Vancouver.
Charles Q. Choi is a science reporter who contributes regularly to IEEE Spectrum. He has written for Scientific American, The New York Times, Wired, and Science, among others.