Two-and-a-half years ago researchers at Chicago-based cyber security firm Infracritical set out to measure how many industrial control systems are openly exposed to the Internet. Their disquieting findings are up for discussion today at the 2014 ICS Cyber Security Conference in Atlanta.
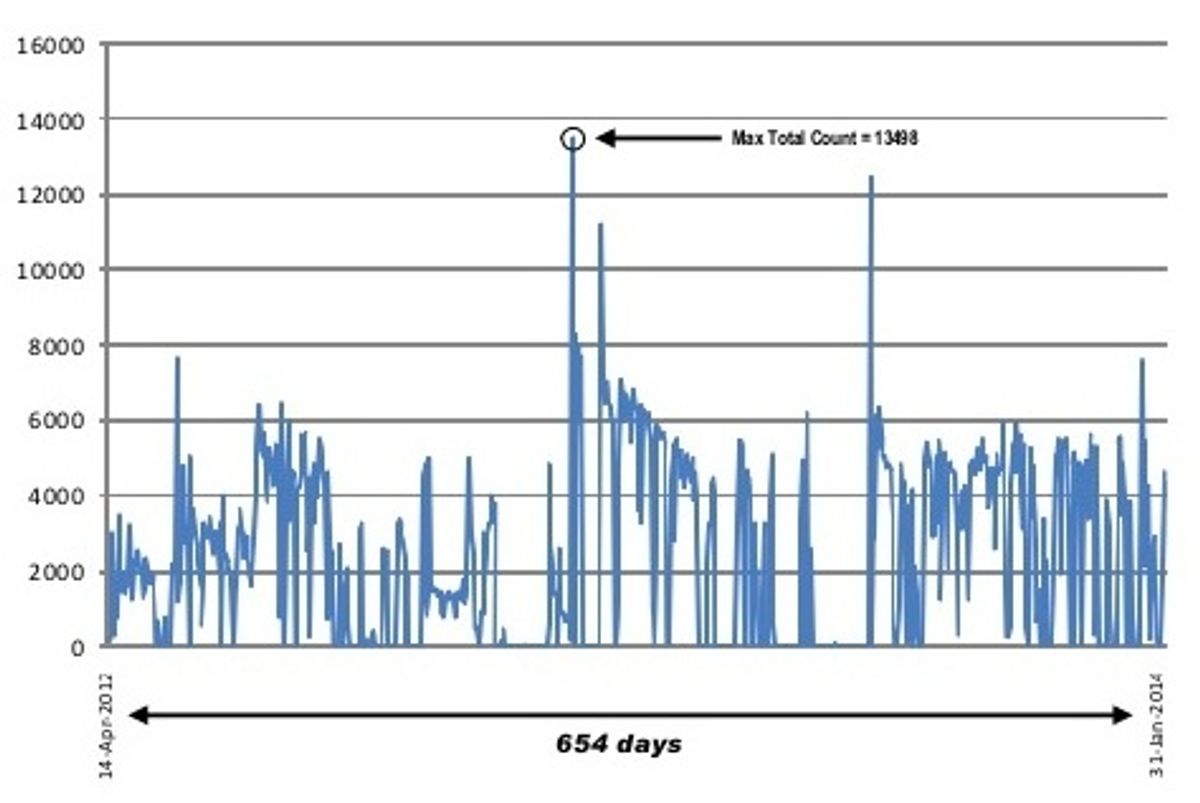
Infracritical remotely identified over 2.2 million unique IP addresses linked to industrial control systems at energy-related sites including electrical substations, wind farms, and water purification plants. And they were still logging an average of 2,000-3,000 new addresses per day when they closed the count in January 2014.
"We never reached bottom," says Infracritical cofounder Bob Radvanovsky, an expert in securing supervisory control and data acquisition (SCADA) systems.
It has long been known that many infrastructure control systems are connected to the Internet. Radvanovsky, a self-professed critical infrastructure evangelist and cyber security mad scientist, and his colleague Jacob Brodsky are among the first to measure that vulnerability and to risk legal attack by naming the vendors whose equipment shows up.
To get answers they relied on a publicly-accessible search engine called Shodan that sniffs out and catalogues Internet-connected devices. Infracritical's project SHINE (for SHodan INtelligence Extraction) built search queries for Shodan using the names of 182 SCADA suppliers and their leading products.
Additional SHINE search terms sought out devices that hackers have used as back-doors to sensitive networks, such as the industrial air conditioning controls linked to the cyber-breach at retailer Target that compromised 70 million credit cards last year.
The list of discoverable devices documented by SHINE reads like a who's-who of top manufacturers, including SCADA and energy management system vendors Siemens, EnergyICT, and Honeywell. Many devices revealed not only their presence but also hardware and firmware metadata that could help a hacker zero in on documented security flaws.
Radvanovsky acknowledges that shifting IP addresses mean there is some duplication in SHINE's count. But he argues that new devices accounted for most of ongoing detections during SHINE's 21.5-month search, and their resulting inability to establish a baseline number of exposed devices.
For one thing, Radvanovsky and Brodsky continued adding search terms during the project as they became aware of additional vendors or as vendors added products.
Shodan's limitations may also have slowed the discovery of both new and pre-existing devices. Though Shodan has been running since 2009, it has what Radvanovsky describes as a "very slow and methodical" ingestion process. "Shodan is not aggressive like Google. That leads us to believe that not all devices have been encountered," says Radvanovsky.
At today's talk Radvanovsky planned to discuss a new project that measures the pressure facing Internet-exposed devices. Initiated last Monday, Infracritical's RUGGEDTRAX project provides a honey-pot for hackers: a Siemens Ruggedcom serial-to-Ethernet converter, whose web interface is "lightly configured" in keeping with the devices discovered through project SHINE.
"In less than two hours it was subjected to a brute force attack from IP addresses appearing to be originating in China. By Thursday morning we'd counted over 4,000 attacks," says Radvanovsky.
Peter Fairley has been tracking energy technologies and their environmental implications globally for over two decades, charting engineering and policy innovations that could slash dependence on fossil fuels and the political forces fighting them. He has been a Contributing Editor with IEEE Spectrum since 2003.