The Ridiculous Amount of Energy It Takes to Run Bitcoin
Running Bitcoin uses a small city’s worth of electricity. Intel and others want to make a more sustainable blockchain


Bitcoin “miners” are electromagnetic alchemists, effectively turning megawatt-hours of electricity into the world’s fastest-growing currency. Their intensive computational activity cryptographically secures the virtual currency, approves transactions, and, in the process, creates new bitcoins for the miners, as payment.
And it does another thing, too: It uses an absolutely stunning amount of power. The ever-expanding racks of processors used by miners already consume as much electricity as a small city. It’s a problem that experts say is bad and getting worse.
“The concern that people continue to debate is, where does this end?” says Michael Reed, head of blockchain technology for Intel.
The Bitcoin leech sucking on the world’s power grids has been held in check, so far, by rapid gains in the energy efficiency of mining hardware. But energy and blockchain analysts are worried about the possibility of a perfect storm: Those efficiency gains are slowing while bitcoin value is rising fast—and its potential transaction growth is immense.
There’s a silver lining, though: This troubling energy picture is inspiring innovators such as Reed to come up with energy-saving approaches that would unleash the technology behind Bitcoin, allowing it to expand into applications for which it was never intended [see “Blockchains: How They Work and Why They’ll Change the World,” in this issue]. Developers of blockchains for such disparate applications as health care management and solar-power trading see Bitcoin’s energy-intensive design as a nonstarter and are now crafting more sustainable blockchains.
To understand these new blockchains, first consider the existing ones. A blockchain is a list of transactions—a ledger—maintained by a community of users, rather than a central authority. It’s called a blockchain because new transactions are bundled into “blocks” of data and written onto the end of a “chain” of existing blocks describing all prior transactions.
That process of chaining blocks together provides the security that has made Bitcoin hack-proof. But the process of writing new blocks, called mining, consumes a lot of energy, for several reasons. One is that each block of transactions must be encoded in an iterative process called cryptographic hashing, which is computationally intensive. It produces a hash, which is a string of characters of fixed length, and it must begin with a specific number of zeros.
Here’s why that takes a lot of computing. Blocks are created by transforming the data associated with a group of transactions. That transformational process, known as hashing, isn’t inherently computationally intensive. But to get a hash that starts with the required number of zeros—it changes (typically increasing) after every 2,016 blocks or roughly every two weeks—a miner has to tweak the data and then hash it, check whether the result has the proper number of zeros, and, if not, start over again. That process of hashing and rehashing usually goes on thousands of times and consumes lots of energy.
The first miner on the network to find a valid hash uses it to create a block, adds it to the chain, and is then rewarded for this community service with newly minted bitcoins. With many parties competing to win each block, no one party can gain control over the currency and its ledger.
Bitcoin’s mining-based ledger-writing process is aptly known as “proof of work.” In June, the world’s bitcoin miners were generating roughly 5 quintillion 256-bit cryptographic hashes every second, according to the all-things-Bitcoin website Blockchain.info. That’s a 5 with 18 zeros after it, every second. No entity tracks how much power it takes to sustain that level of computation. But estimates by independent researchers suggest it’s around 500 megawatts—enough to supply roughly 325,000 homes [PDF] —with the activity concentrated in China and a few other countries with cheap energy and, in some cases, loose regulations on emissions.
Because of all that calculation, the energy cost of Bitcoin is high in comparison with that of conventional financial transactions. For example, according to one estimate, processing a bitcoin transaction consumes more than 5,000 times as much energy as using a Visa credit card.
Mining power is high and getting higher, thanks to a computational arms race. Recall that the required number of zeros at the beginning of a hash is tweaked biweekly to adjust the difficulty of creating a block—and more zeros means more difficulty. The Bitcoin algorithm adds these zeros in order to keep the rate at which blocks are added constant, at one new block every 10 minutes. The idea is to compensate for the mining hardware becoming more and more powerful. When the hashing is harder, it takes more computations to create a block and thus more effort to earn new bitcoins, which are then added to circulation.
“If you try to work harder, the algorithm makes it more difficult,” says Harald Vranken, a computer scientist at Radboud University, in Nijmegen, Netherlands. “It’s a very circular game.”
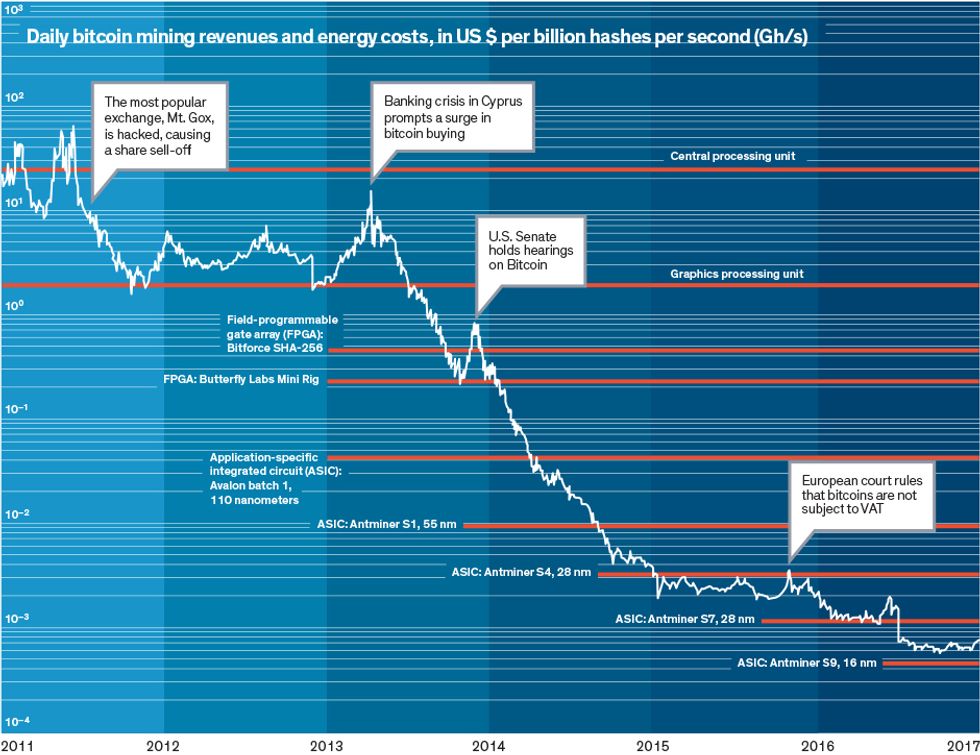
Vranken says doing today’s calculations would “consume way more power than is generated on the entire planet” if it were done using the CPUs available when Bitcoin launched in 2009. What has prevented such disruption is a series of hardware upgrades: Miners began abandoning the CPU for the more-efficient graphics processing unit around 2011, and by 2013, chipmakers were producing application-specific integrated circuits (ASICs) just for bitcoin mining.
Today’s state-of-the-art Bitcoin ASICs complete a 256-bit hash 100 million times as fast and with one-millionth the energy of a 2009-vintage CPU, Vranken says. Yet more efficiency gains are possible by optimizing data centers from the ground up to power and cool bitcoin-mining ASICs [PDF] [see “Why the Biggest Bitcoin Mines Are in China,” coming soon in this issue].
The problem is that chip efficiency gains are slowing [see “Moore’s Law Might Be Slowing Down, But Not Energy Efficiency,” IEEE Spectrum, April 2015] and, according to Vranken, are losing ground against Bitcoin’s exponentially rising exchange rate and rates of hash computation. Another Dutch researcher, Sebastiaan Deetman, says an “enormous increase in hash rate” over the last year or so has likely pushed Bitcoin’s global draw closer to 700 MW.
And if the hash computations accelerate further? In that case, Deetman, who is a doctoral candidate in industrial ecology at Leiden University, sees Bitcoin power demand ballooning 20-fold—to 14 gigawatts—by 2020. If that happens, Bitcoin will be using as much electricity as Denmark.
In certain places, Bitcoin’s power drain may already be straining grids. Mining took off recently in Venezuela, where bitcoins make an attractive alternative to the bolivar, largely worthless now because of hyperinflation. Earlier this year, Venezuelan authorities shut down a mining operation whose 11,000 computers were allegedly running on power that was being siphoned illegally. The drain apparently caused a backlash amid the country’s severe electricity shortages.
Intel’s Reed says that Bitcoin’s sustainability in terms of power usage is tough to predict. He cites such factors as the periodic reduction in the number of bitcoins that miners earn for adding a block. “It’s a very complex set of inputs,” he says.
What Reed is sure of, however, is that the world’s power infrastructures could not handle many more blockchains running on Bitcoin’s computationally intensive proof-of-work mining scheme.
He notes that the leaders of Ethereum—the world’s second most popular cryptocurrency, which started trading in 2015—are planning a switch to a noncompetitive alternative algorithm called proof of stake. Instead of miners battling for block-hashing rights, the network would assign block-adding rights to “forgers” based on their relative holdings of Ethereum currency (known as ethers). This scheme would slash Ethereum’s energy footprint by eliminating the mining process and its computational arms race.
Reed’s team at Intel is working on a novel energy-saving blockchain system that relies on security features built into the chipmaker’s CPUs. Intel’s Hyperledger Sawtooth blockchain software randomly selects which users will write each block. Its proof-of-elapsed-time scheme idles all users’ code for randomly determined intervals. The first to awaken adds the latest transactions to the blockchain and wins compensation.
What prevents participants from tampering with the code to get a larger share of the blocks, says Reed, is that they must run Sawtooth code on Intel CPUs equipped with its Software Guard Extensions (SGX) technology. SGX combines protected areas of memory for code execution with a remote system for verifying its sanctity, enabling Intel to determine whether code has been tampered with.
Several blockchain application developers have signed on, Reed says, including PokitDok, a provider of platforms for sharing health care data. Ted Tanner, PokitDok’s chief technology officer and cofounder, expects several applications by the end of 2017, including an identity-validation system to link patients with their medical records and automatic adjudication of some health insurance claims.
At Cornell University, meanwhile, researchers are using Intel’s SGX to one-up the chip giant. Team leader Ittay Eyal says their system fixes an unintended waste-encouraging aspect of Intel’s blockchain scheme, which his team calls the stale-chip problem. Miners in Intel’s proof-of-elapsed-time scheme will have a financial incentive to use the cheapest SGX-enabled CPUs available, predicts Eyal. This will extend the use of outmoded, inefficient CPUs, he says.
Eyal’s team presented its alternative code [PDF] in May. In their proof-of-useful-work system, participants win blocks by getting credit for doing their own work-related computations within the SGX. A pharmaceutical firm, for example, could run simulations of molecules interacting and simultaneously establish its block-writing status. The firm would want to use the fastest chips available rather than outdated chips, Eyal argues. This preference, his group estimates, should make proof-of-useful-work blockchains at least 25 times as efficient as Intel’s.
Eyal says that lower-energy-consumption blockchains relying on secure hardware will support many applications. But he predicts that such blockchains will not find favor with security-obsessed cryptocurrency users. “The Bitcoin community will not be open to trusting Intel—or anyone else, for that matter,” Eyal declares. In other words, blockchain technology writ large may have a sustainable future, but the power-sucking Bitcoin leech will probably remain ravenous for the foreseeable future.
This article appears in the October 2017 print issue as “Feeding the Blockchain Beast.”