The Hidden Dangers of Chop-Shop Electronics
Clever counterfeiters sell old components as new, threatening both military and commercial systems
On 17 August 2011, Boeing warned the U.S. Navy that an ice-detection module in the P-8A Poseidon, a new reconnaissance aircraft, contained a “reworked part that should not have been put on the airplane originally and should be replaced immediately.” In a message marked “Priority: Critical,” the company blamed the part, a Xilinx field-programmable gate array (FPGA), for the failure of the ice-detection module during a test flight.
How could this have happened? Xilinx, based in San Jose, Calif., is a highly respected manufacturer of FPGAs, and Boeing bought the ice-detection module containing the suspect part from BAE Systems, a reputable British defense company. The trouble occurred somewhere in the supply chain upstream from BAE, which wound through companies in California, Florida, Japan, and China. However, retracing that FPGA’s path led not to Xilinx but to a Chinese company called A Access Electronics. It apparently had turned a quick profit by selling used Xilinx parts as new. BAE ended up purchasing about 300 suspect FPGAs, many of them untested. Fortunately, most had not yet been installed on planes.
To a suspicious buyer, a number of clues might have suggested that the parts were not brand new. For example, parts stamped with the same manufacturing lot code had different ceramic package shapes and four different date codes. Some of the pins were shorter than the length specified in the manufacturer’s data sheet. Some packages themselves were chipped. But somewhere along the supply chain, someone accepted used parts as new, and they ended up on U.S. Navy airplanes.
This incident, described in a hearing held by the U.S. Senate Committee on Armed Services in November 2011, is only the tip of the iceberg. The global trade in recycled electronics parts is enormous and growing rapidly, driven by a confluence of cost pressures, increasingly complex supply chains, and the huge growth in the amount of electronic waste sent for disposal around the world. Recycled parts, relabeled and sold as new, threaten not only military systems but also commercial transportation systems, medical devices and systems, and the computers and networks that run today’s financial markets and communications systems.

Usually, it’s good to recycle electronics products. Ethical recycling companies properly dispose of the toxic ingredients in discarded computers, printers, mobile phones, and other systems and harvest the precious metals they contain. But not everyone in the electronics recycling ecosystem acts ethically.
In theory, with proper screening, electronics components could be safely reused in some low-cost applications, such as calculators and remote controls, where tolerances aren’t particularly demanding. But given the low cost of electronics parts for those products, such reuse wouldn’t usually be worth the trouble. There’s far more economic incentive to use recycled components as replacement parts in more expensive systems with long service lifetimes.
But sometimes old components are misused. Some companies have built a business model based on pulling old parts from cast-off products and reselling them as new. Relabeled or otherwise altered parts masquerading as new can fail prematurely in critical systems, such as those in airplanes and cars, with potentially catastrophic results.
A savvy consumer can often tell with a glance whether a designer handbag or a pair of shoes is genuine or counterfeit. But electronics counterfeits, hiding deep within products and systems, are not so easy to detect. Very few of us open up gadgets to inspect the components inside, and even if we did, almost none of us would know how to distinguish good components from bad. Unethical recyclers of electronics parts don’t need to fool everyone in a supply chain; often they just need to fool a single company among the many that sit upstream from an end product.
Today’s supply chains are built largely on trust. Company A sells a part to Company B and warrants that it will function as specified. Company B may then incorporate that part into a subsystem and sell the subsystem to Company C, in turn warranting that the subsystem will perform as designed. A part can pass through a half dozen or more different intermediaries before it ends up in a finished product. To move undetected through this chain, recycled parts need only function well enough to pass a few tests that are conducted along the way—tests usually designed to weed out accidental defects and design flaws, not to identify parts that counterfeiters have specifically altered to masquerade as something they are not.
Most known cases of electronics parts counterfeiting have been uncovered by military supply chain investigations, sometimes triggered when a key component fails. In part, that’s a reflection of the mismatch between broader electronics-industry obsolescence cycles, which may be as short as one or two years, and the life cycles of defense systems, which may sometimes be decades. A market for replacement parts that were last manufactured a decade ago creates ample opportunity for unethical suppliers to relabel and resell scavenged parts.
But that’s not the whole story. The P-8A Poseidon aircraft, for example, is a relatively new platform, so it’s not just old systems that are targeted. Military-systems manufacturers find counterfeit parts more often than do their commercial brethren, in part because they test more often and more rigorously—they need to do so to make sure the parts will work under extreme conditions. And under a U.S. law in place since the end of 2011, U.S. government contractors are obliged to be more diligent in screening parts destined for military systems, in an effort to identify potential counterfeits.
There’s much less screening going on in the commercial community, and the consumers and businesses that purchase electronics devices and systems are often unaware of the potential risks posed by the parts they contain. Recycled parts may get into the consumer- product supply chain as well and just go undetected, although this is less likely when companies manufacture products in large volumes and purchase parts directly from their manufacturers or their approved distributors.

Recycled parts are just one segment of a vast and fast- growing counterfeit electronics industry. In 2011, the Semiconductor Industry Association pegged the cost of electronics counterfeiting at US $7.5 billion per year in lost revenue and tied it to the loss of 11 000 U.S. jobs. The problem isn’t limited to the United States; electronics counterfeiting is a global concern.
Besides improper recycling, counterfeiting also includes parts that are made in an authorized production run but fail testing and are sold anyway instead of being destroyed, excess inventory intended for the scrap heap that isn’t disposed of properly, and some parts that are simply phony from the beginning and don’t work at all. But the most pervasive problem is recycled parts, accounting for 80 to 90 percent of counterfeit parts in circulation, according to a 2010 estimate by SMT Corp., based in Sandy Hook, Conn.
The U.S. government has long recognized the risks posed by counterfeit parts. A 2010 U.S. Department of Commerce report on counterfeit electronics in the Department of Defense supply chain noted that between 2005 and 2008 the number of companies reporting incidents involving counterfeit chips more than doubled. In February 2012, market-intelligence firm IHS iSuppli stated that “reports of counterfeit parts have soared dramatically in the last two years,” with “1363 separate verified counterfeit-part incidents” reported worldwide in 2011.
In some instances, counterfeit parts end up in high- performance military systems like the Boeing aircraft. In another case that’s become public, an investigation led by a branch of the U.S. Department of Homeland Security shut down Florida-based VisionTech in 2010 and arrested several of its executives. The prosecution charged certain individuals at VisionTech with importing thousands of shipments of confirmed or suspected counterfeit parts from China that had been improperly marked as military grade, some of which were purchased by Raytheon Missile Systems and installed on circuit boards intended for use in a radar-detection system on F-16 aircraft. Fortunately, Raytheon was able to identify the presence of the counterfeits during testing of the boards and didn’t install them in the planes.
In 2011, the U.S. Senate Committee on Armed Services collected data [PDF] on 1800 cases involving a million suspect parts. The committee investigated about 100 of those cases and found defective parts in the supply chain for the Air Force C-17 military transport, the Marine Corps CH-46 helicopter, an Army missile defense system, and more. The committee asked the Government Accountability Office to set up a fake company to purchase electronic parts for military systems online. The GAO found suppliers willing to sell components having imaginary part numbers, and even when the GAO provided real part numbers, the parts it received were counterfeit.
To Catch a Counterfeit
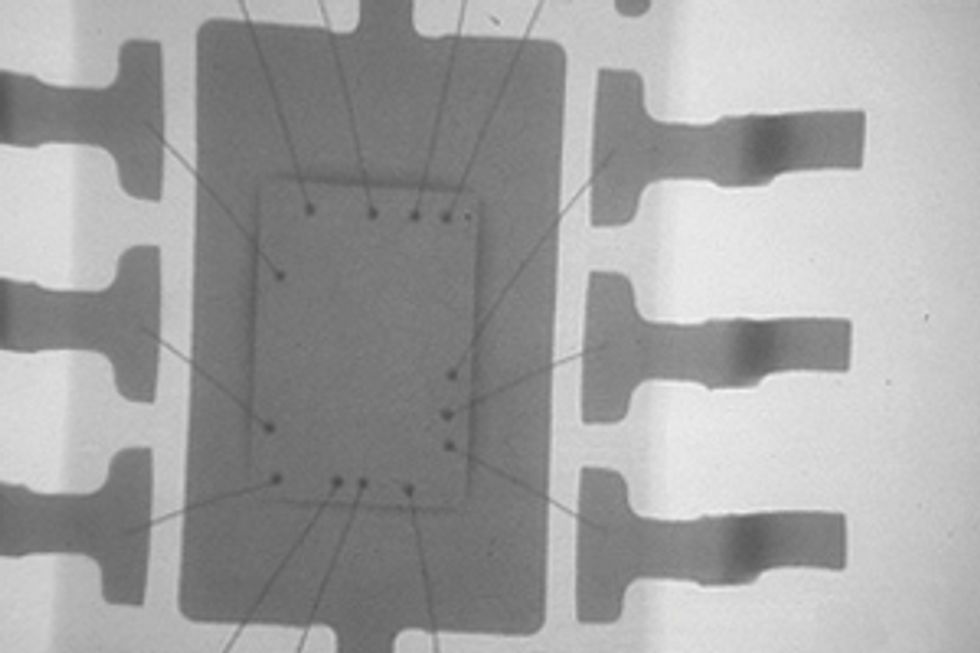
Investigators at SMT Corp. use a variety of signs to spot a counterfeit component. Some counterfeits can be detected by just a visual inspection, but spotting some sophisticated alterations requires other tests.

The counterfeiting scam begins at the foot of a mountain of discarded electronics products that grows by some tens of millions of tons annually.
To harvest the components, recyclers heat circuit boards to a temperature high enough—sometimes up to 400 °C—to melt the solder that attaches them to the boards. Unethical recyclers with little concern for how components will later be used may then bang the boards repeatedly against a hard object to dislodge the parts, which they clean and then sort by size, package style, number of pins, part number, and manufacturer name.
Parts that emerge from this process with their labels and pins undamaged go promptly back into the supply chain, and a dishonest components distributor can quickly sell them as new. If, however, extracting the components damages the labels or pins, there’s more work to do. Pins are simple to straighten, and labels can easily be changed. Unethical distributors often alter even undamaged labels to falsely indicate that a part has a higher performance or operating range than it actually does.
To relabel a part, the distributor sands off the original markings and applies a black coating—a “blacktopping”—that’s almost indistinguishable from the original topcoat. Traditionally, recyclers used blacktopping materials that resembled paint; these could be detected using a simple test such as swabbing the part with acetone, which would dissolve the coating. In 2009, however, SMT discovered that counterfeiters had developed sophisticated blacktop materials that were chemically more similar to the origi nal coatings and therefore much harder to detect. Once a new blacktop coating is in place, the counterfeiter relabels the parts by printing new text onto the blacktop coating, and the recycled parts are ready to sell.
Parts that emerge from this process pose many risks. First, to state the obvious, they are no longer new. This means that expectations regarding performance and lifetime are off. Second, the removal process itself, which exposes parts to high heat, water, chemicals, physical impacts, and other stresses, can damage them. Third, fraudulently labeled parts may end up in the hands of unsuspecting buyers, who use them in unsuitable operating environments where excessive temperature, humidity, or vibrations could lead to premature failure.
Technology offers some solutions to the counterfeiting problem. Companies can scrutinize packages for signs that pins have been straightened or indications that labels have been sanded or repainted. They can also perform more detailed analyses, using X-ray, scanning electron, or acoustic imaging to look inside a package for things that might be amiss, like the improper placement of a chip within its package.
Another telltale feature is a chip’s electrical behavior. Age makes transistors sluggish, so signals can take longer to pass from one portion of a chip to another. Statistical analysis of these path delays and other electrical attributes can play an important role in counter feit detection.
Applied DNA Sciences, based in Stony Brook, N.Y., is taking another step to make it easier to detect counterfeits: It’s mixing DNA synthesized from gene sequences found in plants into the ink used to stamp chip packages. The company keeps the specific gene sequences used to mark chips a secret so that few people can make or verify the marks.

Even the most sophisticated technological countermeasures face challenges. As Tom Sharpe, vice president of SMT, observes, “Our industry has gotten much better at detecting counterfeits—but the counterfeiters are getting better as well.”
In this cat-and-mouse game, the economic equation gives an advantage to the unethical distributors and the recyclers who supply them with parts. They buy discarded components for a song and then sell them at full price. They can then use some of the profits to finance the R&D that makes them ever better at hiding evidence of recycling. Legitimate component buyers and sellers, by contrast, often have razor-thin profit margins. Testing adds to their costs, which may put buyers who perform careful counterfeit-detection testing at a competitive disadvantage compared with buyers who do little or no testing. It would be even more costly, and in most cases impractical, for companies that buy subsystems to test every component within them.
It’s bad enough that these recycled components are increasing the dangers for those who operate military airplanes, helicopters, and ships. But from the standpoint of a counterfeiter, the commercial supply chain is in some ways a much more attractive target, because the market is much larger and more diversified, the level of testing is lower, and product life cycles are often shorter. This gives counterfeit parts less time to fail and provides counterfeiters with more opportunities to sell their wares.
The prospect of a commercial electronics supply chain laden with counterfeit parts is sobering: Commercial parts are used in routers, servers, storage hardware, and many other electronics systems that enable the communications, financial, transportation, power, and other critical infrastructure to run smoothly. While it is clearly not practical to subject every commercial chip to the level of testing used for flight-critical military systems, a well-designed, widely used system of randomized testing explicitly designed to detect counterfeit parts in the commercial supply chain could help dramatically. In addition, with such testing we might be able to picture the true scope of the counterfeit electronics problem. That picture, though, is likely to be a grim one.

Technological solutions are indeed vital for detecting counterfeit electronics. But detection technologies can identify problematic components only after they have entered the supply chain. Truly solving the problem will require making sure that far fewer counterfeit parts enter the supply chain in the first place. That means making it harder for counterfeiters to operate.
To put the squeeze on counterfeiters, we need a better way to track parts as they move through the supply chain and then use that information to call out unethical suppliers. Counterfeiters stay in business because they suffer few or no consequences for their actions. More-effective systems to log, report, and share information about unethical suppliers could put a big dent in their business. Some valuable industry and government counterfeit-reporting programs are already in place; some government agencies collect information about counterfeit incidents and report it to their suppliers. In addition, the Independent Distributors of Electronics Association, for example, keeps a list of suspected counterfeit incidents. But as important as these efforts are, they likely capture information on just a small fraction of the global trade in counterfeit electronics. We need more companies—including those not directly involved in manufacturing systems for government customers—to be aware of the problem and to improve their efforts at detecting, tracking, and reporting counterfeit parts.
We must also address this problem on an international level, and in doing so we must acknowledge the geopolitical realities of the counterfeit-parts industry. Counterfeiters stay in business because they are at the upstream end of an opaque, loosely regulated global market for parts. Trade negotiators need to talk more openly about the risks posed by counterfeit electronic components. Governments can help by closing regulatory loopholes that allow counterfeiters to operate and by increasing whistle-blower protections to encourage reporting. Together, these steps could make it much harder for recyclers and other counterfeiters to operate.
Now that electronic products are everywhere, the threat of recycled electronics parts is everywhere as well. Although we will never be able to eliminate the threat of recycled components completely, we can and should reduce the risks they pose.
A modification to this article was made on 23 September 2013.
About the Author
Over the past 20 years, Villasenor, a professor at UCLA and nonresident senior fellow at the Brookings Institution, has seen globalization benefit the electronics industry. He’s also witnessed an unwelcome by-product: the rise in counterfeit chips. Nowadays, he says, the hardware supply chain is “even more opaque than I and many other people suspected.”
Mohammad (Mark) Tehranipoor, an associate professor of electrical and computer engineering at the University of Connecticut, has been working on issues involving hardware security and trust and counterfeit detection and prevention for the past 10 years. He says, “globalization has brought many vulnerabilities into the hardware underlying information systems. Years ago, no one ever imagined even discussing the kinds of things we have to deal with today in terms of securing hardware.”