Some hackers use software and hardware to express themselves creatively—either solving entirely novel technical challenges or finding new ways to skin the same old cats. Others are motivated by money, power, politics, or pure mischief. They steal identities, deface Web sites, and break into supposedly secure and certainly sensitive databases.
We at IEEE Spectrum have written dozens of stories about both—the Steampunkers and Arduino do-it-yourselfers, on the one hand, the Anonymous and Lulzsec ne’er-do-wells on the other. Inspired by New York Magazine’s Approval Matrix, we took 25 of the biggest and best stories and assessed them along two dimensions: innovation and impact. (Last updated 6 July 2011)
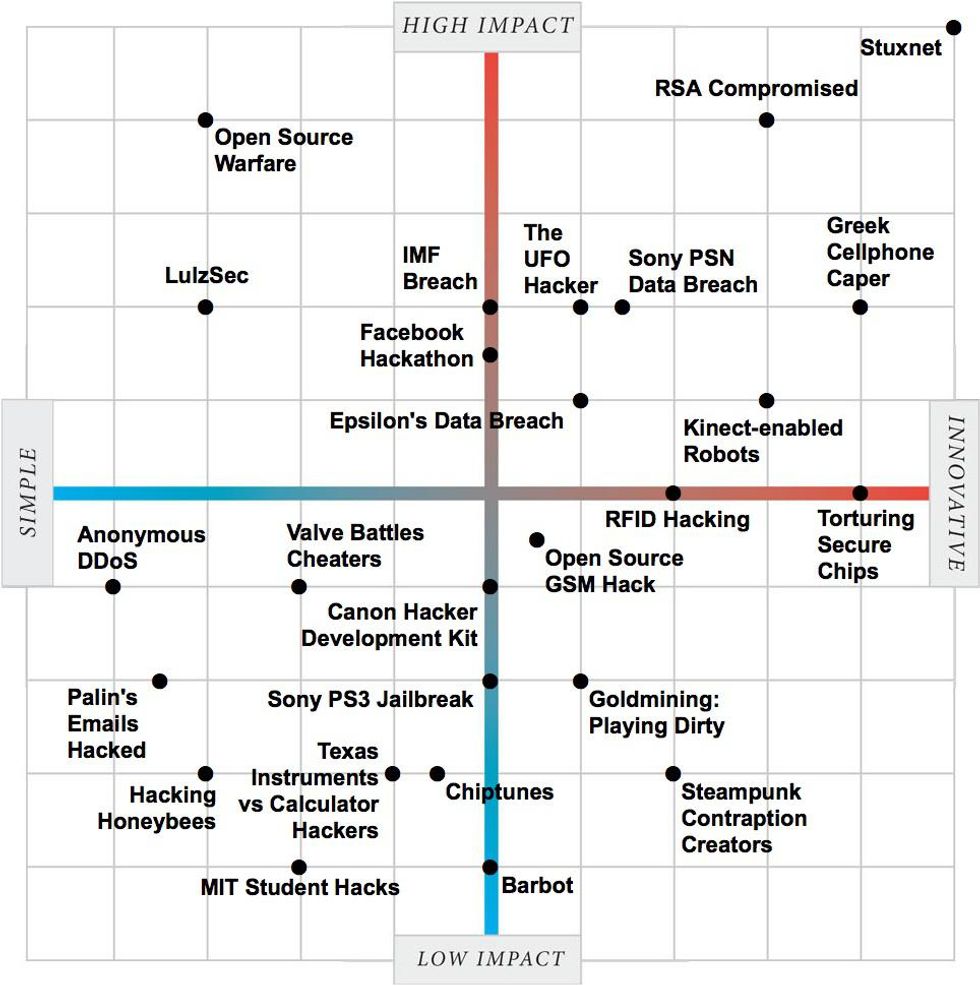
Read all the stories:
Joshua J. Romero is a software developer and journalist. A former IEEE Spectrum senior editor, he holds a bachelor’s degree in astronomy and physics from the University of Arizona and a master’s in journalism from New York University.


