Online Voting Isn’t as Flawed as You Think—Just Ask Estonia
Casting a vote online can be secure and convenient

Virtual Polling Place: Estonia has allowed citizens to vote online through their smartphones or laptops in eight nationwide elections since 2005. In the most recent election, more than 30 percent of Estonians cast their votes online.
The United States has had more than 200 years to get its election process right, but it’s still far from perfect, and the country’s voter turnout is a global embarrassment. For the 2014 midterm election, just 36 percent of eligible voters showed up at the polls, the worst rate in 72 years. The showing was much better in 2012, when 58 percent of the U.S. electorate cast a ballot to choose their next president. But that still puts what is arguably the world’s oldest democracy toward the back of the pack for voter participation among developed countries.
When U.S. voters do make it to the polls, they may encounter long lines, be turned away for showing the wrong ID, or even find their names have been erroneously scrubbed from voter rolls. And special provisions meant to enable military personnel and expats to vote by mail are notoriously inefficient: About 2 percent [PDF] of postal ballots are thrown out because they arrive after the voting deadline.
aspect_ratio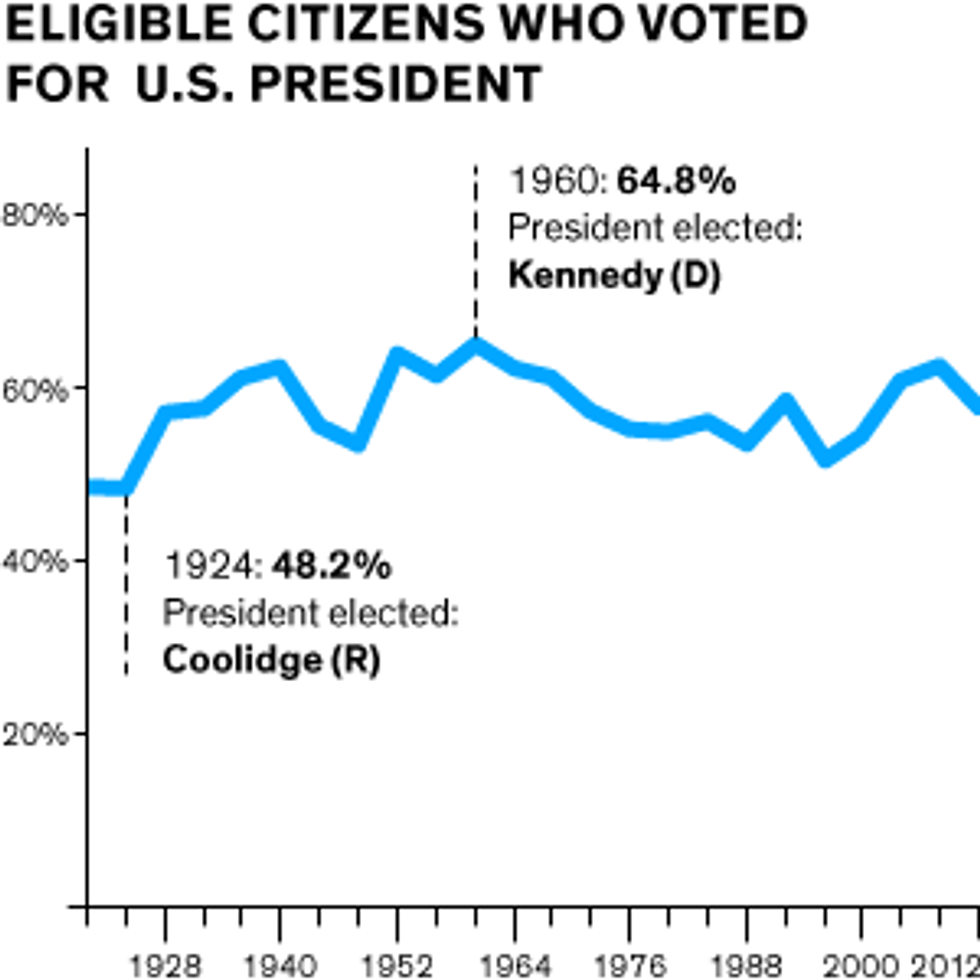
So why can’t U.S. voters vote online? After all, we routinely use the Internet to communicate with each other and conduct a wide variety of transactions. And yet online elections are still very much in their infancy. In the United States, three-fourths of voters will use paper ballots in the presidential elections in November. In fact, most democracies still collect votes in a traditional ballot box, an approach that requires armies of poll workers—or, more recently, automated scanning machines—to tally the results. In recent years, many polling sites have switched to electronic voting on touch-screen computers. These machines improve accessibility for voters with disabilities, but they come with their own vulnerabilities and security holes.
Allowing people to vote instead from their smartphones, tablets, or laptops would have many benefits. First, it would be much more convenient, which might boost voter turnout. Second, it would offer a means to verify that each ballot was cast by an eligible voter. And finally, it would eliminate some of the most common mistakes that occur with traditional ballots, such as counting errors made by tired poll workers toiling late on election night, so the result would be accurate and repeatable.
However, a vocal cadre of cybersecurity researchers and computer scientists think that online voting is not yet ready for prime time. They see online voting systems as more susceptible to hacks and security breaches than are traditional processes, and they say that fraud would be harder to control. Some also argue that remote voters—that is, those who cast their ballots from a location other than a central polling spot—may be more subject to coercion than are traditional voters.
To be sure, online voting experiments have not always gone smoothly. In 2010, for example, the District of Columbia Board of Elections rolled out an experimental online voting system for Washington, D.C.’s absentee voters. Prior to election day, the District held a mock election and invited interested parties to attempt to compromise its security. Within 48 hours of the system going live, hackers managed to take control.
Republic of Estonia
Area: 45,228 square kilometers
Population: 1.3 million
Government: Parliamentary republic
Currency: Euro
Source: CIA—The World FactbookPublic fiascos like this have caused many people to rightly question whether the security and integrity of their votes can be ensured, and governments are understandably wary of introducing new technology that hackers might attack. This is particularly true in the United States given recent news that hackers are trying to infiltrate voter registration systems just a few months after the Russian government allegedly hacked the Democratic National Committee.
But there is a way to engineer online voting systems to be secure. Here, the experiences of one country stand out: Estonia. For more than a decade Estonia has offered online voting in parliamentary and municipal elections through a system built by Cybernetica, a leading provider of secure e-government technologies. In 2014, that company joined forces with Smartmatic, a London-based company whose online voting program I direct. Estonia’s experiences prove that well-built systems can offer convenience to the voter while still upholding the fundamental democratic principles of secrecy and fairness. Here’s how.
Online voting has three stages that pose security challenges: registering and authenticating voters; securely transmitting votes to a virtual ballot box and protecting them once they’ve arrived; and verifying that votes have been correctly cast. A good online voting system will have built-in safeguards to minimize risks at all three stages. (By “online voting,” I meanletting people cast their votes on their own digital devices—smartphone, laptop, or tablet—and from their homes, offices, or some other remote location. I don’t mean having to use an electronic voting machine located in a controlled environment such as a polling station, consulate, or embassy, which may be secure but isn’t terribly convenient.)
Sadly, the Washington, D.C., system had security holes in all three stages. The platform lacked advanced cryptographic protection, and it didn’t offer end-to-end encryption with digital signing of votes. There was no way to verify that a vote had been cast. What’s more, the system’s design compromised the secrecy of the cryptographic key used to decrypt each vote. It’s no surprise that the mock election was a disaster.
Compare that failure to the system in Estonia, which has offered online voting to its citizens since 2005. To date, the country has run eight nationwide elections using Cybernetica’s online voting system. And it has been a hit: In the 2015 parliamentary election, over 30 percent of the electorate—or more than 175,000 people—opted to cast ballots online rather than visit a polling station. Citizens as young as 18 and as old as 85 sent electronic votes from 121 countries. In some surveys, as many as 20 percent of Estonian online voters say they would not have voted had they been unable to do so online. One comparative analysis found the online option may have nudged up voter turnout by 2.6 percent [PDF] in 2009. And Estonia’s online voting system has never suffered a security breach or produced a miscount.
Why does the Estonian system work so well? One key reason stems from the government’s decision to begin issuing in 2002 electronic identification cards, which are credit-card-size ID cards embedded with a chip and protected by multiple pass codes. More recently, it has also started to hand out SIM-based mobile IDs linked to citizens’ smartphones. These electronic and mobile IDs are currently carried by 1.2 million Estonians (or 94 percent of the country’s population) and help Estonians file their tax returns and apply for jobs.

Estonia’s electronic IDs also help enormously with one of the hardest tasks in any election: ensuring that only legitimate voters are voting. This is especially challenging for mail-in voting, which has become common in Switzerland and the United Kingdom, and is now the de facto method of voting in Oregon and several other U.S. states. In mail-in elections, a voter typically verifies his or her identity by giving a voter ID number, social security number, or date of birth on a form that’s sent in with the ballot. To impersonate a voter, a thief would simply need to obtain that information and the ballot.
Online voting uses much stronger authentication methods. In Estonia, the government builds a voter profile with several pieces of biographic and biometric data that are stored both in a central database and separately in the person’s mobile and electronic IDs. When Estonians are ready to cast a ballot, they download an app to access the online voting system. To verify their identity, they plug their electronic ID into a USB card reader or enter their phone number to use their mobile ID, and immediately enter a personal identification number, or PIN. The system checks that the biographic and biometric data on the card or device matches all of the information in the voter profile stored by the government. Forging an entire voter profile stored on a unique electronic ID or mobile chip is much harder than scrawling a stolen voter ID number or social security number onto a form.
Ensuring that a voter’s ballot reflects his actual choice is another security challenge. Critics of online voting have argued that voters who cast their ballots remotely, from locations that aren’t monitored or controlled, will be more vulnerable to coercion. This threat can be reduced by letting eligible voters cast as many ballots as they wish, with each new ballot superseding the previous ballot. So a voter who is intimidated or coerced at some point can simply access the system later and cast a new ballot. Estonia takes this strategy a step further by allowing voters who have already voted online to visit a polling station and fill out a traditional paper ballot, which has supremacy over the online vote. Instituting this protection is more a matter of political will than technology, since it’s relatively easy to program an online voting system to permit multiple votes and prioritize them by date.
Once an online ballot is authenticated, it and every other ballot must then be securely transferred to a virtual ballot box to be tallied. This is a crucial step—many experts opposed to online voting argue that hackers would inevitably exploit any security flaws they find in this handoff. However, with the right measures in place, this transfer can be made far safer than, say, mailing a postal ballot in a paper envelope.
The best way to safeguard digital ballots is to use public-key encryption. This cryptographic technique uses two keys—a public key known to the sender (in this case, the voter) and a secret or private key known only to the recipient (that is, the electoral board). It’s the same method that Internet users already trust to keep their emails, online bank accounts, and WhatsApp messages from prying eyes.
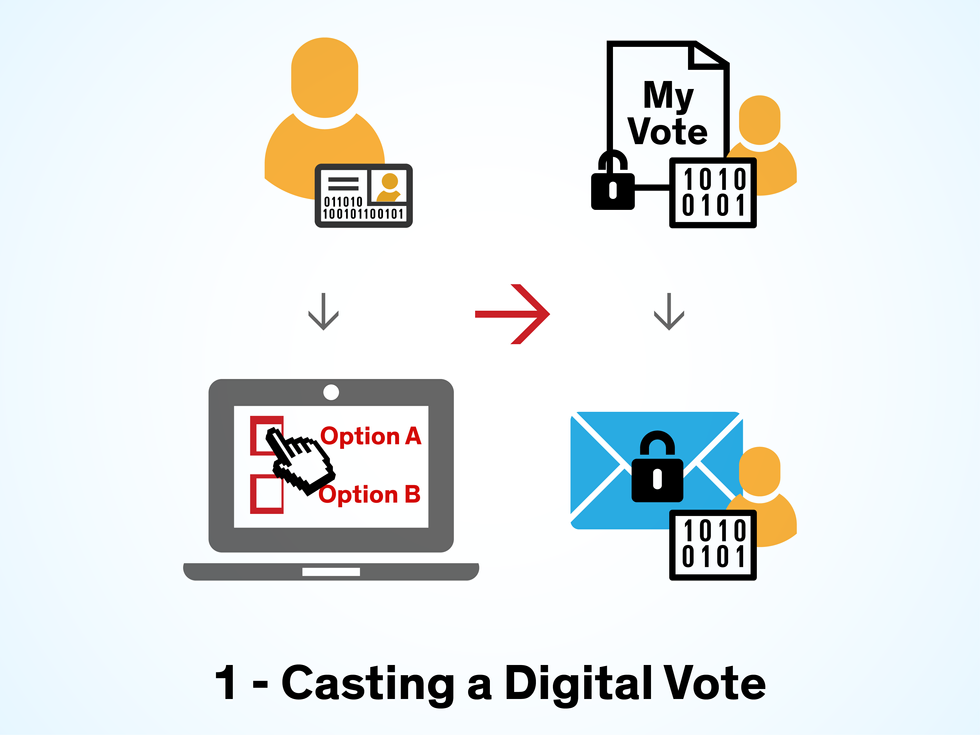
Estonia built public-key encryption into its electronic and mobile IDs. With their IDs, voters encrypt their votes with the public key by entering a second, slightly longer PIN after they vote. Once the ballot is encrypted, the second PIN also allows them to sign it with a unique digital signature in what’s called a double-envelope scheme. The inner “envelope” uses an encryption algorithm to convert each selected candidate’s name (for example, “Jane Smith”) into a jumbled string of digits and letters called ciphertext (for example, 9fkqibn72bfi9dh23t6dgaoevjdg), which only a decryption algorithm held by the electoral board can interpret. The outer envelope uses the same strategy to garble the voter’s name. Thus, the inner envelope maintains the privacy of the vote, and the outer envelope assures that the vote was submitted by an eligible citizen.
Once the ballot is signed and encrypted, the voter sends it to a virtual ballot box through a secure connection that relies on a popular Internet protocol called Transport Layer Security (TLS); PayPal and Facebook, among many others, rely on TLS to protect users’ data. This protocol establishes the connection between the voter’s computer and the election servers using a form of encryption called symmetric cryptography. The voter’s computer or device and the server agree on what’s known as a cipher suite—that is, a combination of authentication and encryption codes as well as key-exchange algorithms that they will both use to securely send messages, prove their identity to one another, and trade random numbers to create a “master secret.” The master secret is a secret number, series of letters, or code that both parties have agreed to use to encrypt their data when they send it to one another. With this secret, the voter’s computer and the server can then generate session keys to encrypt and share data. This is all done at the start of a session before the vote is transferred. The benefit of using symmetric encryption to transfer votes is that it’s faster and requires less processing power than does public-key encryption.
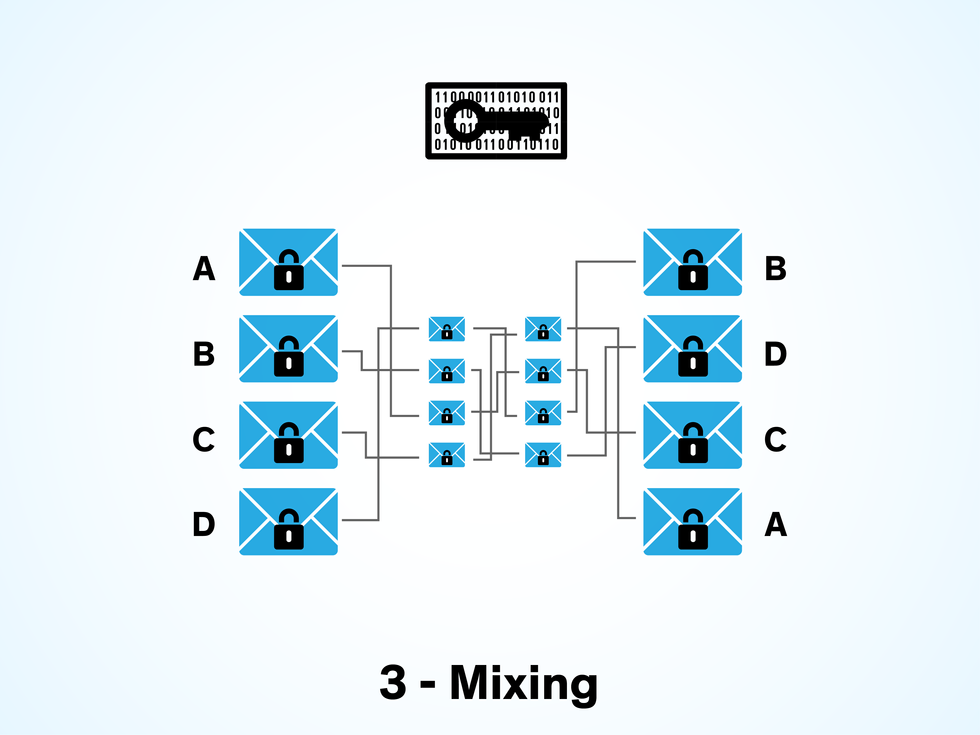
After the votes are safely transferred into the virtual ballot box, they remain encrypted until the election has closed. Then, the system strips the ballots’ outer envelopes to reveal the inner envelopes containing the encrypted votes. The votes are then shuffled to randomize the order in which they were cast, thereby protecting voter anonymity by making it difficult for an eavesdropper to reconnect a vote to its digital signature. The cryptographic shuffling is normally achieved by passing the encrypted votes through a mixing network, or “mixnet.” In a mixnet, message routing protocols send messages (in this case, votes) through a chain of servers or nodes, with each node accepting messages from the other servers, wrapping them in a fresh set of ciphertext, and sending them in a randomized order to the next node in the chain. For a typical online election, each vote is mixed by three to five nodes.
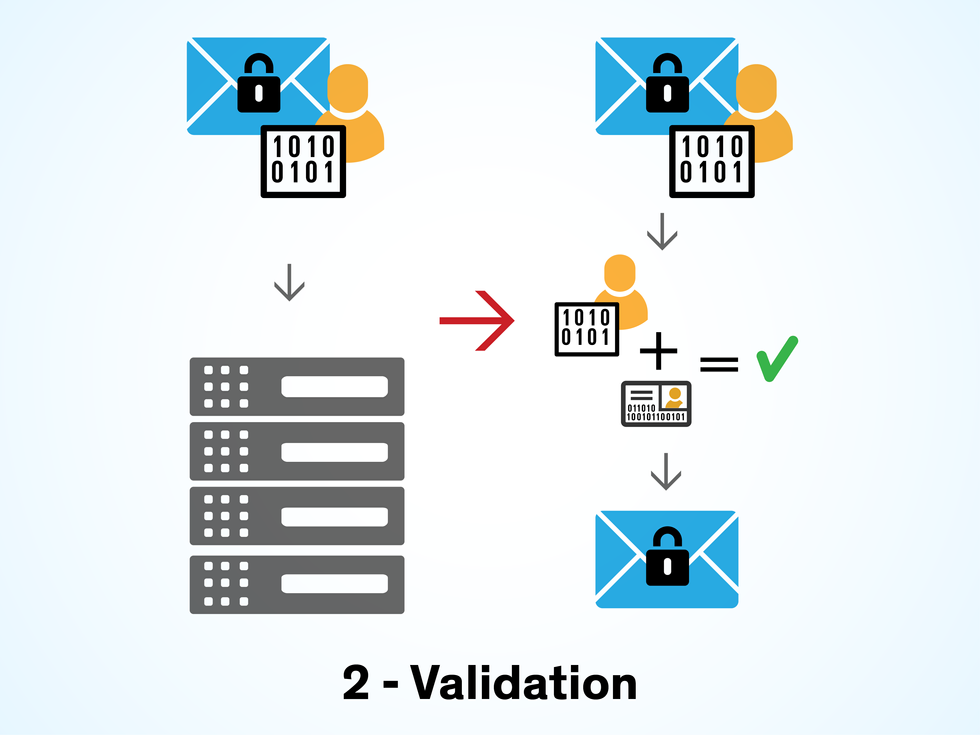
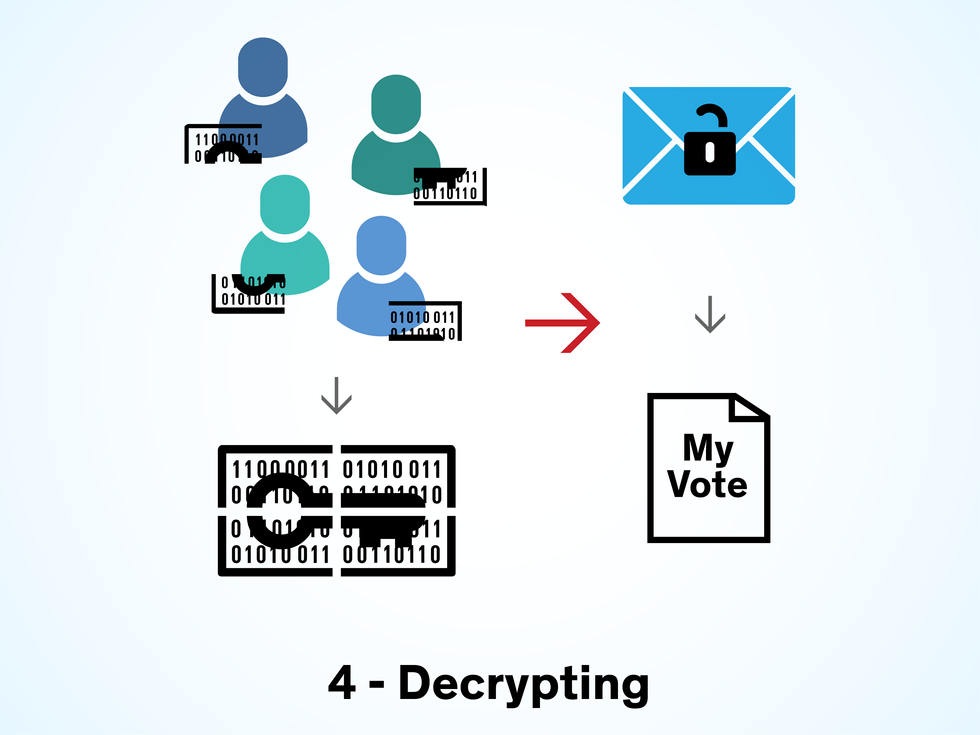
Once the digital votes are mixed, they are transferred to an air-gapped decryption server—a computer physically isolated from all networks—where they are prepared for counting. The votes can be decrypted only using the election private key, which marks the final step of the public-key encryption process. Clearly, this private key would be of great interest to anyone who wanted to sabotage an election. That’s why in the Estonian system, the private key can be generated only by bringing together members of the electoral board and reaching a quorum, in what is referred to as an M-of-N threshold decryption scheme.
With this scheme, the private key is divided into pieces that are distributed among a set of PIN-protected tokens, such as smart cards or secure USB devices. The tokens are then given to seven or (N) members of the electoral board. After the polls close and the votes are mixed, the board members meet at the election office and insert their tokens into the decryption server. They each enter the PIN to unlock their token, and their share of the election private key is read and combined with the other shares to recreate the private key. The private key can be generated only by a quorum of electoral board members (M). In Estonia, that is no fewer than four members. Without the reassembled key, it’s impossible to decrypt the votes.
1. To cast an online vote in Estonia, a voter logs in with an electronic ID and makes a selection. The vote is encrypted and digitally signed in a “double envelope” scheme.

All of this mixing and decrypting takes a fair amount of processing power. That could get expensive for a country as large as the United States, whose population is almost 250 times that of Estonia. But my company estimates that the availability of mass computing power and cloud services could radically reduce the processing cost to no more than US $200 for mixing and decrypting votes within an hour of the close of polls—and that’s assuming a 100 percent turnout of every U.S. citizen of voting age. You’d need the equivalent of 40 Amazon Web Services’ m4.10xlarge virtual servers to run a U.S. presidential election in this manner. That said, civic leaders will probably be reticent to jump straight into using cloud computing for online voting. More likely, the jurisdictions in each state, and in some instances individual counties, would want to purchase their own servers and infrastructure for online voting, and doing so would radically increase the cost.
One concern that many people have about online voting is that these systems will make it easier for an attacker to compromise a large number of ballots much faster than would be possible through a paper ballot or mail-in system. It’s true that such a risk is greater with online voting systems. But the fact that U.S. elections are highly decentralized, with votes tallied separately in thousands of counties and townships, has always ensured that any major technical or security issue that arises in one location will not compromise millions of votes. This is the case whether the problem is a faulty electronic voting machine, a grievous miscount of paper ballots, or an attack on an online voting system.
The final step in the electoral process is to count the online votes. In Estonia, this is done automatically by a separate set of air-gapped servers, which are physically isolated from other components of the online voting system. At Smartmatic, we conduct logic and accuracy tests to ensure that our systems correctly tally votes; that involves feeding each voting system test ballots that we have already counted and then checking the results. In 16 years of running large-scale electronic elections, our systems have never erroneously counted a ballot.
By contrast, the estimated error rate for paper ballots is in the range of 0.5 to 2 percent. In the U.S., the error rate for automated scanning and electronic voting machines is required by the Federal Election Commission to be much smaller—around 0.00001 percent, or one ballot in 10,000,000 [PDF], though some systems have returned error rates that are much higher [PDF]. To be sure, independent analyses comparing the error rate for online voting to those of other methods are still needed, as are large-scale tests to simulate an online election as large as a U.S. presidential election.
By now, I hope I’ve convinced you that end-to-end encryption can provide robustprotection for the privacy and integrity of online ballots. But a skeptical voter may still wonder: If I cast my ballot remotely, how can I be sure that it has reached the ballot box intact? It’s an excellent question, and online voting vendors, including Smartmatic, have responded by developing mechanisms to prove that the security protocols are operating correctly.
Here’s how it works in Estonia: Let’s say the voter casts her ballot on her laptop. The server receiving the ballot generates a unique voting receipt that’s displayed as a QR code on the laptop. The voter can then scan the QR code using a smartphone app, which displays the contents of the vote that was logged on the server. The voter can easily see that her vote was successfully and accurately cast.
Using a smartphone to verify a vote cast on a laptop, or vice versa, also mitigates potential “man-in-the-middle” attacks in which the voting device itself is compromised by a hacker. Any would-be attacker would need to institute a coordinated attack on both the voting device and the verification device, which would be extremely difficult to do. Traditional mail-in ballots, by contrast, give voters no way of verifying whether the ballot has reached its intended destination unless they pay for certified delivery. Even then, they don’t know if the ballot was read correctly or simply tossed out because they forgot to sign the envelope.
Building in the capability to verify votes does raise another concern: traceability. In e-commerce or online banking, a user’s identity is permanently linked to financial information within the system. But in an election, it’s critical that no one is able to trace a vote back to the voter. Several of the measures previously described, including public-key encryption, digital signatures, and the mixnet, are designed to prevent traceability.
Smartmatic has also been researching blockchain techniques to add transparency to elections without compromising voter privacy. A blockchain is basically an accounting system that relies on a community of users to record transactions and post them to a public bulletin board that is available to anyone online. Each new transaction adds a block to the chain, and the legitimacy of each transaction is evaluated by every user based on algorithms they’ve agreed upon. A transaction is added to the chain only once it has been verified by a majority of users. Rather than being kept in just one place, a copy of the blockchain is stored on every user’s server so that no single user can alter it without other users finding out.
In one test, we demonstrated the ability of anonymous users to verify their votes using a blockchain. As an online vote is cast, a cryptographic hash function is used to render the vote as a hash digest—that is, a string of bits of a fixed length. The hash digest is then posted as a new block in a blockchain on a public bulletin board. By finding her digest on the bulletin board, a voter can verify the presence of her vote without anyone else knowing which vote she cast. At the same time, it’s impossible for anyone to add, remove, or modify a block without corrupting the blockchain. After the polls close, a separate vote-counting application creates its own blockchain from the votes in the digital ballot box. That blockchain should match the public bulletin board’s blockchain, proving that the online voting system has operated correctly.
Experiments in Online Voting
Plenty of local governments and political groups have tried online voting, and their experiences haven’t always been positive:
- Norway ran online voting trials in 2011 and 2013 but discontinued them because of security concerns and a lack of evidence that they increased turnout.
- The Utah Republican Party offered Smartmatic’s online voting program to members choosing their 2016 presidential candidate. The party’s online registration process confused some voters, but overall turnout set a new record high for Utah caucuses.
- In a 2012 election for political party leadership in Canada, a denial-of-service attack stalled the party’s website and delayed a vote.
While this mechanism seems promising, there have been several recent high-profile security breaches involving blockchains used to exchange digital currencies including Bitcoin. And some other early blockchain experiments, also for purposes other than online voting, struggled to scale up as the number of transactions grew. Even if those issues can be resolved, the decentralized nature of blockchains means that no single user holds more trust or power than any other, so they are unlikely to be popular with most election officials, who would prefer to retain full control over the digital ballot box.
Although there are many reasons to feel optimistic about the future of online voting, there are also plenty of challenges that need to be solved. One remaining problem is that the personal devices that voters use to cast their ballots can become infected with malware that reads their passwords and PIN codes from their keystrokes or that allows hackers to remotely control their desktops. That possibility was among the chief complaints voiced by cybersecurity researchers with the Open Rights Group, a U.K. nonprofit, and the University of Michigan. They critiqued [PDF] Estonia’s online voting system in 2014 and described several potential attacks that hackers might use. The Estonia National Electoral Committee responded to their criticisms shortly after by saying that the theoretical attacks they described were not feasible. Authenticating votes through a secure ID card and providing verifiability to voters should minimize the malware risk.
But these and other risks will always remain a concern for online elections. Indeed, the mission to build secure online voting systems will never end. Internet threats change almost daily, and online voting vendors like Smartmatic must continually invest in research and development to address the evolving challenges.
Given all of this, does the technology exist to enable secure, transparent online voting today? I believe so. That said, I doubt the United States will rush to replace the traditional polling station in the short term. But advances in sophisticated encryption methods such as postquantum cryptography are giving us more effective tools to solve the remaining challenges of online voting. Maybe in 2020, for the first time, we’ll see the U.S. president elected by iPhone.
About the Author
Mike Summers is the program director for Internet voting at Smartmatic, and director of the Smartmatic-Cybernetica Centre of Excellence for Internet Voting. Founded in 2000, Smartmatic is a leading provider of voting technologies and solutions and has managed elections across five continents, processing over 3.7 billion votes. Smartmatic is headquartered in London.


