Banking in Cyberspace: An Investment in Itself
Home banking has evolved from the telephone to dial-up computers and now to the World Wide Web
When home banking was introduced in the United States, in the mid-1980s, the top-of-the-line computer was the IBM PC/XT, which had at most 640KB of memory and a 20-MB hard drive. Fewer than half a million modems were in use, and Hayes had just introduced its 1200-baud model for $350. "User-friendliness" was still an abstract idea, particularly to the in-house bank programmers providing software for home users. Is it any wonder that home banking was such a huge failure?
A short decade later, and how things have changed. Today's standard computer uses a 100-MHz Pentium chip, 20MB of memory, and 1 GB of hard-drive space. New computers now routinely come with 28.8-kb/s modems and CD-ROM drives. Upward of 23 million homes are connected to the Internet. And more and more computers are being used with the new generation of home banking software. More importantly, many new access devices are being developed and brought to market that will transcend the PC-literate and ultimately reach everyone. Web TV is an example.
Even in its dimmest moments, home banking was inevitable. People in the United States have less and less patience for driving to banks and waiting in teller lines. Total non-branch activity is growing at a rate of 15 percent a year. Statistics show that automatic teller machines (ATMs), telephone banking, and computer-based banking account for over 50 percent of all banking transactions today.
Yet the United States has not been as quick as some other cultures to adopt electronic commerce. Electronic banking accounts for an estimated 90 percent of Japan's financial transactions. France's proprietary network, Minitel, with 14.4 million users offers services from more than 10 000 companies. By comparison, only 1 percent of U.S. banking transactions are accomplished by network. But a boom is on the way. Jupiter Communications, a New York City technology research firm, predicts that the proportion of network banking transactions will grow to 6 percent by the end of 1997 and perhaps to 75 percent by the year 2005.
North American banks are getting ready. About 79 percent of them now offer home banking services, ranging from electronic bill payment to portfolio management.
Introducing an Internet bank
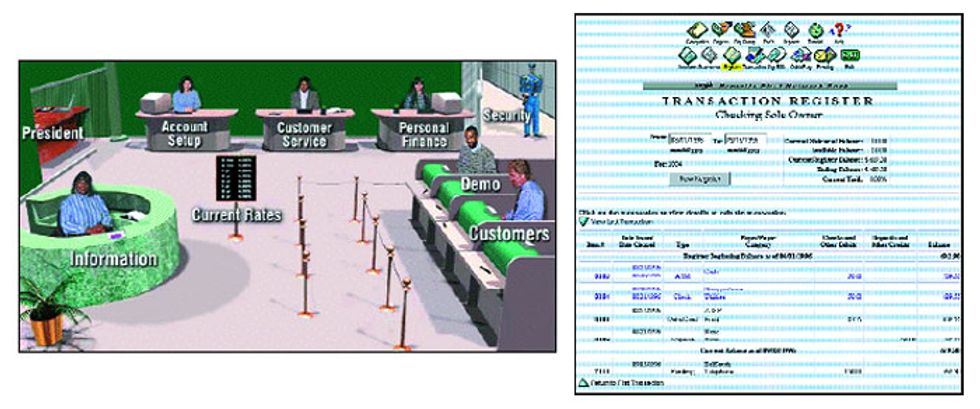
Internet banking is a new concept in the United States. The first financial institution to use the World Wide Web as its primary delivery channel was Security First Network Bank (SFNB), which opened its virtual doors on Oct. 18, 1995 [Fig. 1]. Virtual Financial Manager, the software behind SFNB, is being marketed to financial institutions around the world through its wholly owned subsidiary Security First Technologies, which is a merger of the former Five Paces Inc. and SecureWare Inc. To date, 14 banks--including Huntington Bancshares, M&I Bank, Salem Five Cents Bank, West Coast Savings, the National Bank of Commerce (NCBC), Republic Bank of St. Petersburg, and Australia and New Zealand Banking Group Ltd. (ANZ)--have adopted the package as their front-end processor for Internet access.
Meanwhile, on Sept. 9, 1996, IBM Corp. joined with 15 U.S. and Canadian banks to create the Integrion Financial Network, which will develop a system offering transaction-processing services comparable to those now offered by CheckFree and Visa. These services will be offered through an Internet interface.
Interest in Internet banking is global. In France, for example, 16 banks have Internet home pages. One advantage is lower costs. Electronic payments cut processing fees, since fewer paper checks must be handled. By providing statements and check images on-line, a bank can save a few dollars per account each month on mailings (though paper statements must still be mailed out). Physical overhead expenses are lower, too, since fewer brick-and-mortar branches are needed. And significant savings come from the smaller number of employees needed to service customers: an average electronic transaction costs only pennies, as compared with 54 cents for the average transaction handled over the phone by a combination of voice-response systems and customer call centers, and $1.10 for the average in-person transaction.
For customers, Internet banks can provide 24-hour access to an account, allowing them to pay bills, to categorize income and expenses, to produce cash-flow reports, and to print budgets whenever they please.
Models for e-banking
Three main models of electronic banking have emerged: PC-based banking, or "fat client"; the "thin-clientstateless" architecture; and the "thin-client-stateful" model.
Traditional PC-based banking relies on applications, such as Intuit Inc.'s Quicken or Microsoft Money, that reside on the customer's PC, the client machine. It is sometimes called a fat client because every application requires dedicated software on the PC.
Such home-banking applications store data in a database management system on the local PC. The application can add value to that data (for instance, budget categories or payee lists) and has business logic to organize and present data in useful forms. For example, the customer can tell the application to send an electronic payment for a car note or a mortgage on the 15th of each month. Communicating through an intermediary front-end processor residing on the server at the bank, customers can dial into it at any time to download account information.
While this is a convenient approach, it has drawbacks. With this type of PC-centered interface, customers must maintain the software on their own computers. They are responsible for new releases and upgrades, as well as for downloading and updating information. The connection with the bank can be made only through the computer containing the software. From the bank's point of view, the software manufacturer controls the interface--in essence, the way the bank is presented to its customers.
The second of the models of electronic banking, the thin-clientstateless architecture, runs many applications with only one resident software program: an Internet browser. There is no database storage, no value-added capability and only minimal business logic on either the client browser system or the intermediary front-end processor server. Instead, raw data is simply grabbed from the legacy mainframe, often using "screen scraping" techniques, and then presented via Hypertext Markup Language (HTML) screens to the customer with little or no opportunity for enhanced features or services. This approach effectively dumbs down the browser-based service to the minimal functionality of a voice response system.
A screen scraper performs essentially the same function with a visual interface. The application can be used to pay bills and transfer funds, and it is accessible to the customer via any computer with a network connection. From the bank's standpoint, the interface is inexpensive to build and maintain--particularly since most banks already have a voice response system. The bank's difficulty in adding functionality and value to data will relegate this approach to the low end of Internet banking technology.
Most voice response systems are based on PCs running under IBM's OS/2 operating system. While this architecture can manage 60 000 or more phone inquiries a day, the processing required for Internet presentation is more complex. As the number of Internet banking customers grows, problems could develop if the system is unable to expand.
In the third model of Internet banking, the thin-clientstateful approach, the access device remains a thin client requiring only an Internet browser, so the interface resembles the one used in the thin clientstateless model. But the business logic and database storage kept on the local PC in the fat-client model are moved to the intermediary front-end processor. The term "stateful" refers to the ability to extend and add value to the data, with categories, budgets, payee lists, and so forth. Security First Technologies calls this technology a "consolidation engine."
The thin-clientstateful approach is the new paradigm for Internet banking. It offers the functionality of a PC-based financial manager coupled to Internet access. This model can also consolidate information from disparate systems. Banks have traditionally gathered large amounts of information about their customers. But it is often stored in separate databases in different departments: for example, mortgage applications would be in one database, checking transactions in another. Only recently have banks begun to undertake "data mining," the process of integrating these databases to provide a total financial picture. According to Information Week, 45 of the top 100 U.S. banks had installed data-mining applications by mid-1996, and 50 more were planning to.
To remain competitive in an Internet Age, banks must make better use of data mining by greatly expanding the amount of detailed customer information available to the data analysis software tools. Such information should include loans, brokerage, insurance, and credit cards. Cross selling decisions cannot be made solely on the basis of demand deposit account data.
One example of how a total financial picture might work involves the incorporation of credit cards. Credit card information, maintained by a separate processor, is incorporated into a relational database and electronically integrated with other customer data. The customer's credit card balance, interest fees, and payment history can also be added to the data displayed on screen. This ability to relate host data to transaction records, demographic profiles, and customer preferences allows the bank to give users a customized interface, updated each time they log on.
For example, a customer might ask that credit card balances be automatically paid from her checking account after transferrals from money market accounts, or might want to have certain stocks tracked, or could request stock alerts when certain pricing or trading levels are reached. Each of the three approaches has advantages for certain segments of the population. A few power users will continue to keep dedicated financial management packages on their own PCs, regardless of the interface they use. It is simply uneconomical for a bank to load its server with every specialized capability a power user might desire.
Another segment of the market neither wants nor needs a complex interface. They want only to be able to see their bank balances, pay a few bills, and occasionally transfer money. The thin-client stateless model suits not only their needs but also those of a bank seeking to expand an existing voice response system with an Internet interface.
The thin-clientstateful approach is the one adopted by Security First Technologies for its Virtual Financial Manager, which is used by SFNB and by internal development projects at several large banks, including Wells Fargo and those in the Integrion network.
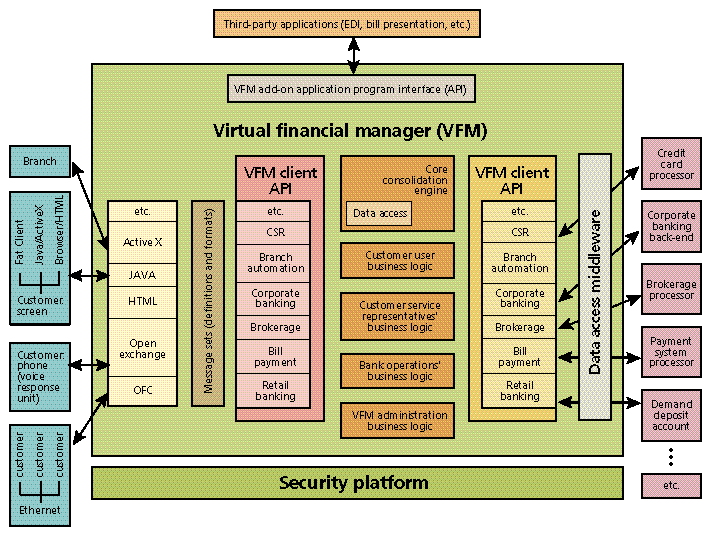
Recognizing the value of all three methods, Security First Technologies adopted a three-tier architecture for Virtual Financial Manager [Fig. 2] so that customers could use it in a variety of ways. To accommodate people who want to maintain personal financial managers on their own computers, Virtual Financial Manager supports all open systems, such as Open Financial Exchange from Intuit, Microsoft, and CheckFree. Customers who want only to see bank balances and pay bills have the option of a simple interface. Those who want more functions can tailor the interface by adding services to the basic ones it offers.
The security question
Security is always an issue when banks consider electronic commerce. In the Security First Technologies model, security procedures begin with the on-line customer application, which is filled out, encrypted, and sent to the bank. The information is verified by a credit-checking service. No credit report is run, but the file is checked to ensure that the information provided (Social Security number, name, and address) is consistent with the material on file. This step ensures that the applicant is serious--not just someone playing with the site by entering false information.
For the same reason, a physical copy of the application and a signature card (required by law) must be mailed to the bank. An account-creation package with the user name and the account password is mailed to the customer to confirm the postal address. (This package may eventually include a personal authentication device such as a smartcard or a floppy disk holding an encrypted private key, and a certificate of authentication associating the customer with it.) The account is then set up.
Customers communicate with the bank via a World Wide Web browser. Every transaction sent to the bank from within the bank's Web site is automatically encrypted. The bank server receives the transaction, decrypts the message, and undertakes the service requested. The only requirement is that the customer's browser must support the Secure Sockets Layer (SSL) protocol, the security standard for most browsers and on-line services.
The bank server utilizes a "trusted" operating system derived from Security First Technologies' CMW+ compartmentalized-mode workstation, a multilevel, military-grade security system modified for commercial use (it is now owned by Hewlett-Packard Co. and marketed under the trade name VirtualVault). SFNB is the first non-governmental application of trustedoperatingsystem technology. VirtualVault provides a hierarchy of authorizations and privileges that protect the system's functions from outside interference.
The administrator of a traditional Unix system would use an account called root, which grants access to all areas of the system. By contrast, a trusted operating system replaces the root account with a privilege mechanism, which uses explicit rules for granting privileges to specific processes. The privilege mechanism limits users' actions to the commands each has been authorized to use. Unrecognized users or unfamiliar applications are denied privileges and cannot gain access.
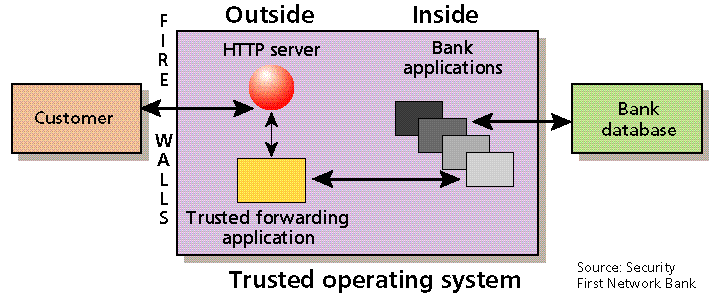
An information-separation mechanism in the trusted operating system creates a wall between the network environment and internal bank applications. The network receives and validates the user's requests. A trusted forwarding application then routes them to the internal bank environment, where they are processed and passed back [Fig. 3].
Because of this separation, nothing in the outside environment can touch banking functions, and no outside process can disrupt the bank's internal operations. This feature protects it against any security breach, accidental or malicious, occurring in the Web server.
The final safeguard of the system, providing accountability for all internal procedures and attempted break-ins, is its audit mechanism, which records suspicious activity, including the use of privileges, access violations, logins, logouts, and unsuccessful network connections.
Firewalls, routers, and the Internet
Further protection from intruders is provided by a system of firewalls and filtering routers, each presenting an additional barrier between the Internet and the internal bank network. To check the source and destination addresses on each network packet and determine whether to let it through, filtering routers are connected to both the outside Internet and to an organization's internal network, or intranet. Each address is checked against an internal database for authenticity; for example, to prevent outside users from masquerading as internal sources, the filtering router eliminates any outside packet with an inside source address.
Firewalls work in a similar way, examining each packet of information sent across the Internet to the customer service network. Using proxy software, they provide singlepoint-of-access controls and auditing facilities, serving as a barrier between internal and external computers. If an outside host wants to access an internal computer, the host communicates with the firewall, and the firewall communicates with the internal computer, thus protecting inside addresses from outside access.
For retail commerce, Security First Technologies chose the SSL protocol, which uses encryption to provide a secure channel for the data flowing between the browser and the bank server. The protection provided by SSL ensures the confidentiality of financial and personal data.
Most security breaches involve a password violation. For this reason, Internet banking customers are prompted to periodically change their passwords. If an unauthorized user does manage to obtain someone's password and break into that account, potential damage is limited by the audit trail. Only very foolish thieves would send electronic payments to themselves. Also, the time and expense required to break into an account far exceeds the potential benefit.
Threats and countermeasures
Several kinds of attacks could be mounted against a network bank. An intruder might try to break into the bank application by pretending to be an administrator or a customer service representative--in other words, by attempting to send data packets that appear to come from an inside machine. This type of attack--network address spoofing--would be foiled by the filtering router, which drops outside packets with an inside source address.
User identity spoofing is another possibility. All customer identities and passwords reside in a database on the bank server, so no one can pretend to be a bank customer; inaccurate passwords or unrecognized identities are denied access. Because the password is sent encrypted by SSL, transactions are safe as long as customers ensure the secrecy of their own passwords.
An attacker might also try to break into the bank's database and alter or add customer passwords. But an outside attacker will not have access to those databases, because they are stored in the internal environment, protected by the trusted operating system's separation mechanism. Furthermore, access to these databases is limited by the trusted operating system's privilege mechanism.
Finally, a common attack against network platforms involves replacing network services with Trojan Horses--software that may subvert the machine on which the service runs. A trusted operating system minimizes the amount of damage such a rogue program can cause. First, the filtering router eliminates all but SSL-protected HTTP traffic. The HTTP server also examines each information packet before calling the trusted forwarding application to send the request to the bank. Any packet containing HTML code that could be used to run malicious programs is eliminated during these steps. Finally, all processes run with the minimum set of privileges necessary, greatly limiting the extent of any possible breach. The firewall limits traffic to customer service machines to e-mail only, reducing the chance that an unauthorized program could be introduced to the system by that route.
Although the possibility of external attacks causes the most talk, a bank is more at risk from an attack by an employee or someone with access to the internal server. To secure against this, Security First Network Bank uses HannaH, trade name for a network security product developed by Security First Technologies.
HannaH, developed as a tool to help corporate users create their own private networks across the Internet, provides strong authentication, permitting users to identify the server machine or PC being accessed. Access control can be configured to restrict access to or from hosts, subnets, network services, and users. The system immediately detects any attempt to insert, modify, or destroy network traffic and provides a detailed audit, so that attacks can be traced as they occur.
All transactions are documented by the trusted operating system. Customer service PCs also run a special virus protection program, Troy, so that no unauthorized software can be added to a machine and no code can be introduced through the floppy drive.
An Internet bank insured by the Federal Deposit Insurance Corp. (FDIC) is subject to the same Federal regulations as other kinds of banking institution. Federal auditors visit regularly to verify the physical security of the site and assess the administration, data management, and programming. Internal process regulations have needed few adjustments for Internet-based banks. One of the few new rules requires every link from the bank's Web site to any other address on the Web to be verified to prevent inappropriate links or implied relationships not meeting regulatory standards.
Some regulations may need to be changed for Internet banks. Reg E, for example, stipulates that in every electronic transaction, the customer must be able to receive a receipt--as at an ATM--and that each transaction must be verified by a written statement in 30 days. In an Internet bank, the account register, updated with account activity, is the statement. A statement mailed once a month not only costs the bank more than it does to maintain the account but is outdated when it arrives.
Another regulatory requirement is the Community Reinvestment Act, which requires banking institutions to participate in and support the communities they serve. For Internet banks, the problem is not compliance but the definition of "community." Since an Internet bank may have customers in all 50 states through its virtual branch, enforcing of the Community Reinvestment Act presents a puzzle for regulators.
The final regulatory issue concerns the entire banking industry. The growing number of nonbank financial service providers, such as credit card companies, e-pay systems, and smartcard vendors, are free of Federal bank regulations. Rules for banks should be reviewed to keep up with changes in financial technology. Where technologies can become obsolete in 18 months, and where at least two years are needed to implement new regulations, problems may arise if strong measures are not adopted soon.
Technology marches on
Currently, average modem speeds top off at 28.8 kb/s, which can make Internet access discouragingly slow. Integrated-services digital network (ISDN) lines can soon bring Internet access to homes at rates of 64128 kb/s. Other technologies such as asymmetric digital subscriber line and cable modems will soon offer speeds at 500 kb/s and higher.
In parallel development are Web browser "appliances" already being introduced to market. Fast dial-tone browsers will eventually make the Internet as readily available as the dial tone of a telephone. These browsers are entering gear like TV sets and phones, and they serve as vehicles for paging, sending e-mail, placing phone calls, and so on. This is not an incremental change for the banking or other industries. The Internet will fundamentally change how we do business.
Soon, surfing the Web will be as simple as channel surfing on television. When Joe Couch Potato can do his banking during the football game's commercials, electronic commerce will have reached critical mass. That day is right around the corner.
Note: Virtual Financial Manager and Troy are registered trademarks of Security First Technologies.
About the Author
Michael C. McChesney is chief executive officer of Security First Network Bank's wholly owned subsidiary, Security First Technologies, Atlanta, Ga. (formerly Five Paces Inc. and SecureWare Inc., which he cofounded in 1994 and 1986, respectively). Previously, he was a senior associate at Investments Orange Nassau, Boston, responsible for venture capital investments for the $50 million fund.