New Security Technology Detects Malicious Cyberattacks on Drones, Cars, and Robots
Mitsubishi Electric has developed an algorithm that measures inconsistencies in multiple sensors to thwart malicious manipulation
Sensor-based automatic control technology is now used in hundreds of applications as varied as vehicle accident prevention, agricultural monitoring, and self-balancing robots. But as sensor interaction with the environment increases to enable control systems to “see,” “listen,” and “sense” their environment more accurately, the potential for cyber attacks also grows.
To counter this danger, Mitsubishi Electric has developed what it believes is the first sensor-security technology for detecting inconsistencies that appear in sensor measurements when a system is under attack. Development was supported by Japan’s New Energy and Industrial Technology Development Organization (NEDO).
A key component in automatic control systems is sensor fusion technology. It works by combining the data from a number of sensors to produce more accurate information than if data were taken from individual sensors and used separately. For example, by combining the data from multiple sensors in a car, the result provides a more precise estimate of the car’s speed, which in turn improves better control over performance and reliability.
“Until now, it was thought that sensor fusion algorithms were robust and could not easily be attacked because they integrate data from several sensors,” says Takeshi Yoneda, a manager at Mitsubishi Electric’s Information Technology R&D Center in Ofuna, 60 kilometers south of Tokyo. “Also, because sensor fusion algorithms are complex, it’s been difficult to evaluate how secure they are in real-world testing.”
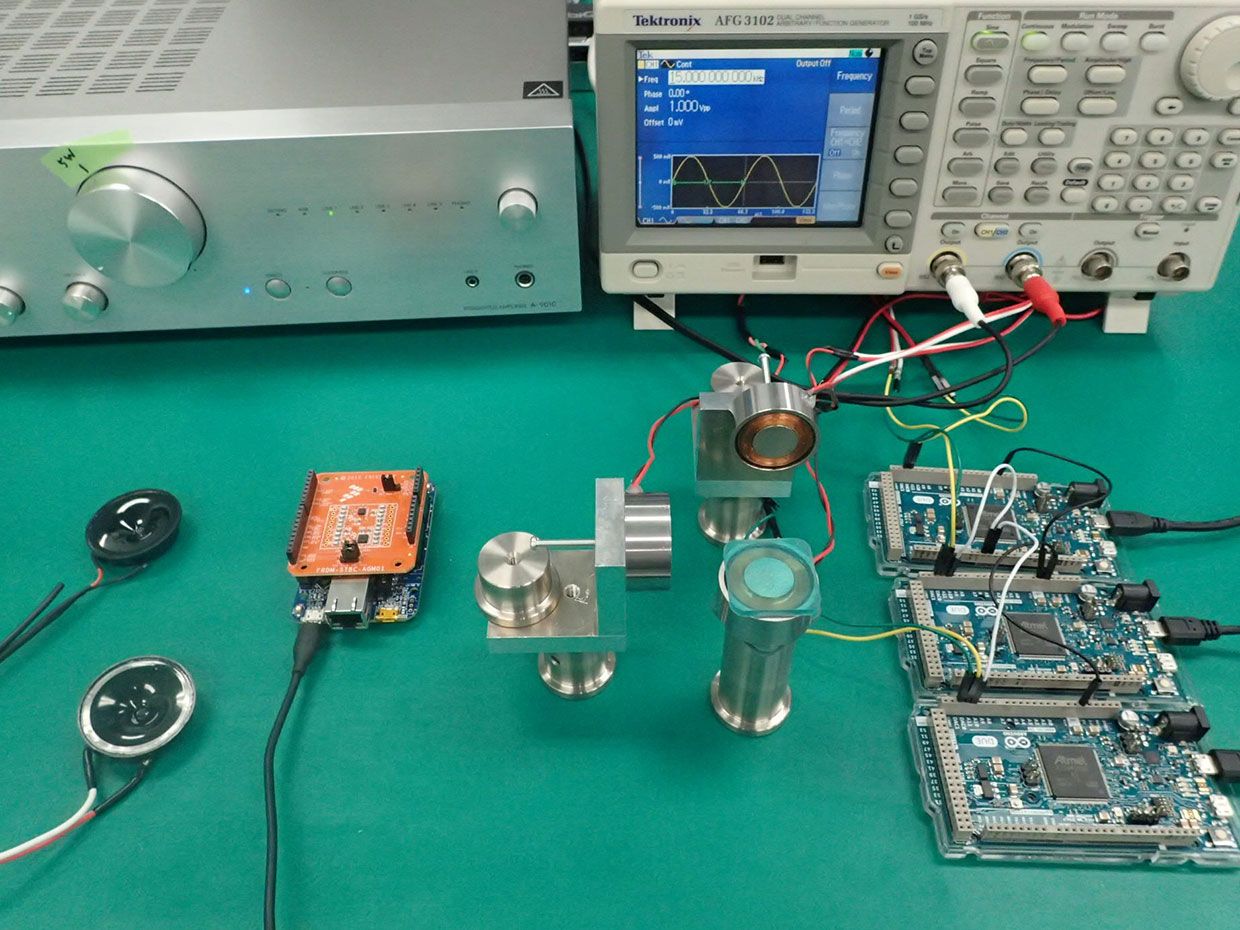
As a result, he says no effective countermeasures to cyber attacks on sensor fusion systems have been developed. To test the vulnerability of these systems, Mitsubishi researchers have set up an experimental evaluation environment that subjects different sensors to various kinds of cyber attacks. Accelerometers and gyroscopes, for instance, are susceptible to acoustic wave interference, while magnetometers can be attacked using a magnetic signal generator.
At a Mitsubishi Electric technology open house held this February, researchers used a small drone to demonstrate how the attack detection algorithm works.
To remain stable and on course during flight, most drones employ a gyroscope, accelerometer, and a magnetometer. Data from the accelerometer and magnetometer are combined and compared in real time to data from the gyroscope. Under normal conditions, Yoneda says the two results have a high correlation, and any difference between the two is corrected using a smart filter such as a Kalman filter. The new combined result is then used by the sensor fusion algorithm to produce accurate inclination data to control the drone’s roll, pitch, and yaw.
In circumstances where the combined accelerometer and magnetometer data experience intermittent noise from the environment or the drone itself, the control system blocks out those inputs, using only the data from the gyroscope until the situation returns to normal again.
“It’s because this mechanism appears reliable, that sensor fusion systems are believed to be robust when it comes to noise or attack signals,” says Yoneda. “However, we’ve now shown these systems can be attacked.”
In previous testing, the researchers used an evaluation board that had an inclination sensor employing a gyroscope, accelerometer, and a magnetometer. For the Open House demonstration, the researcher used a programmable drone for the first time. However, they could not obtain a suitable drone for the demonstration that included a magnetometer, so only the accelerometer was initially subjected to an ultrasound attack.
The attack created a large enough discrepancy between the accelerometer and gyroscope data that the attack-detection algorithm, embedded in the sensor fusion algorithm software, detected the sustained variation between the two data sets and kicked in. The result: The fusion algorithm relied solely on the data from the gyroscope as the drone switched over to fail-safe mode and landed safely before any damage was done.
In a second demonstration, lacking the attack-detection algorithm, the gyroscope and the accelerometer were attacked with separate ultrasound signals. The control system attempted to control the drone’s attitude using the fake signals, became confused, and the drone tumbled to the ground.
“It was my colleague, Shoei Nashimoto, who first understood sensor attacks were interfering with inclination data,” says Yoneda. “When you know this, the countermeasure is simple enough to implement, and it can be applied to sensor fusion control systems in general. So it can be used with lots of applications.”
Yoneda also points out that the detector algorithm is compact—just a few tens of lines of code. “This means we can implement it at low cost because there is no need to modify the hardware.”
Mitsubishi aims to commercialize the technology next year; it will use it in its own products and likely license it to other manufacturers of cars, drones, and humanoid robots to begin with.