Quantum Cash and the End of Counterfeiting
Physicists say they can make money that can’t be copied—at least in theory
Since the invention of paper money, counterfeiters have churned out fake bills. Some of their handiwork, created with high-tech inks, papers, and printing presses, is so good that it’s very difficult to distinguish from the real thing. National banks combat the counterfeiters with difficult-to-copy watermarks, holograms, and other sophisticated measures. But to give money the ultimate protection, some quantum physicists are turning to the weird quirks that govern nature’s fundamental particles.
At the moment, the idea of “quantum money” is very much on the drawing board. That hasn’t stopped researchers from pondering what encryption schemes they might apply for it, or from wondering how the technologies used to create quantum states could be shrunk down “to the point of fitting it in your wallet,” says Scott Aaronson, an MIT computer scientist who works on quantum money. “This is science fiction, but it’s science fiction that doesn’t violate any of the known laws of physics.”
The laws that govern subatomic particles differ dramatically from those governing everyday experience. The relevant quantum law here is the no-cloning theorem, which says it is impossible to copy a quantum particle’s state exactly. That’s because reproducing a particle’s state involves making measurements—and the measurements change the particle’s overall properties. In certain cases, where you already know something about the state in question, quantum mechanics does allow you to measure one attribute of a particle. But in doing so you’ve made it impossible to measure the particle’s other attributes.
This rule implies that if you use money that is somehow linked to a quantum particle, you could, in principle, make it impossible to copy: It would be counterfeit-proof.
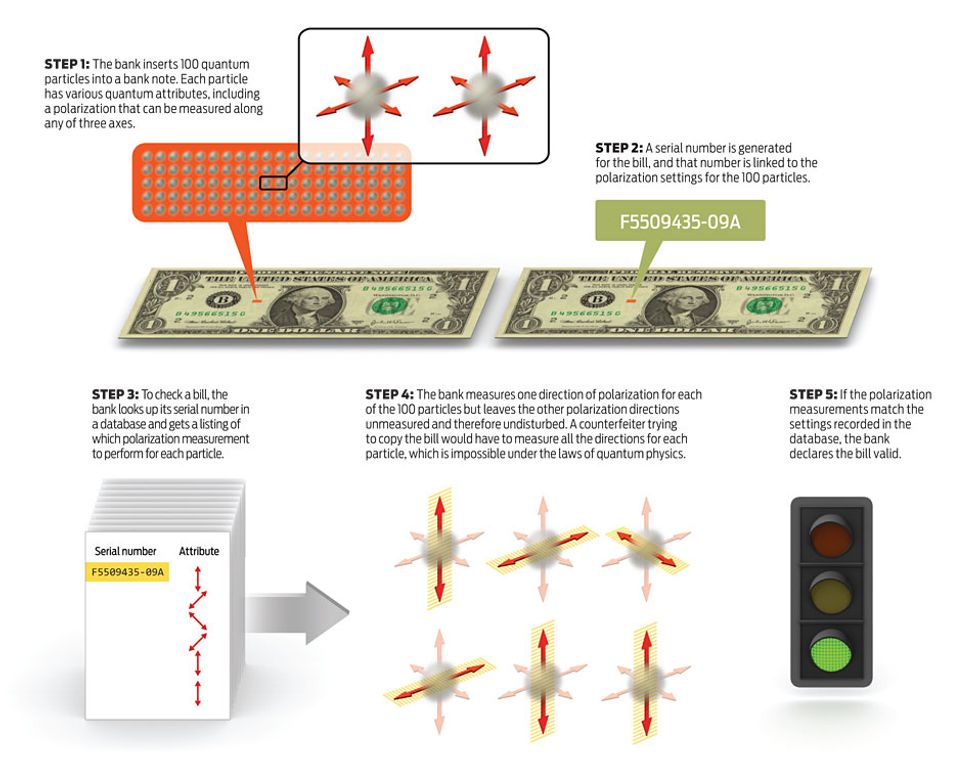
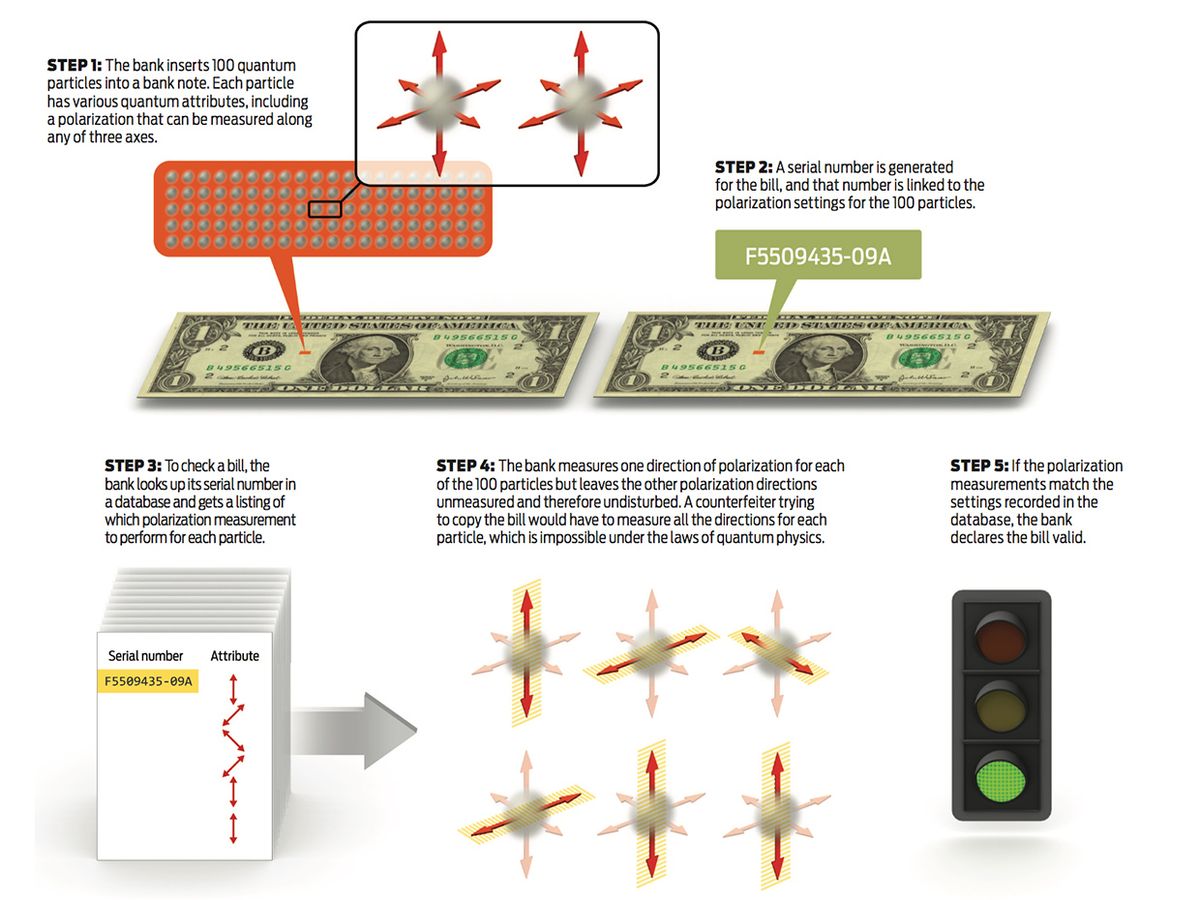
The visionary physicist Stephen Wiesner came up with the idea of quantum money in 1969. He suggested that banks somehow insert a hundred or so photons, the quantum particles of light, into each banknote. He didn’t have any clear idea of how to do that, nor do physicists today, but never mind. It’s still an intriguing notion, because the issuing bank could then create a kind of minuscule secret watermark by polarizing the photons in a special way.
To validate the note later, the bank would check just one attribute of each photon (for example, its vertical or horizontal polarization), leaving all other attributes unmeasured. The bank could then verify the note’s authenticity by checking its records for how the photons were set originally for this particular bill, which the bank could look up using the bill’s printed serial number.
Thanks to the no-cloning theorem, a counterfeiter couldn’t measure all the attributes of each photon to produce a copy. Nor could he just measure the one attribute that mattered for each photon, because only the bank would know which attributes those were.
But beyond the daunting engineering challenge of storing photons, or any other quantum particles, there’s another basic problem with this scheme: It’s a private encryption. Only the issuing bank could validate the notes. “The ideal is quantum money that anyone can verify,” Aaronson says—just the way every store clerk in the United States can hold a $20 bill up to the light to look for the embedded plastic strip.
That would require some form of public encryption, and every such scheme researchers have created so far is potentially crackable. But it’s still worth exploring how that might work. Verification between two people would involve some kind of “black box”—a machine that checks the status of a piece of quantum money and spits out only the answer “valid” or “invalid.” Most of the proposed public-verification schemes are built on some sort of mathematical relationship between a bank note’s quantum states and its serial number, so the verification machine would use an algorithm to check the math. This verifier, and the algorithm it follows, must be designed so that even if they were to fall into the hands of a counterfeiter, he couldn’t use them to create fakes.
As fast as quantum money researchers have proposed encryption schemes, their colleagues have cracked them, but it’s clear that everyone’s having a great deal of fun. Most recently, Aaronson and his MIT collaborator Paul Christiano put forth a proposal [PDF] in which each banknote’s serial number is linked to a large number of quantum particles, which are bound together using a quantum trick known as entanglement.
All of this is pie in the sky, of course, until engineers can create physical systems capable of retaining quantum states within money—and that will perhaps be the biggest challenge of all. Running a quantum economy would require people to hold information encoded in the polarization of photons or the spin of electrons, say, for as long as they required cash to sit in their pockets. But quantum states are notoriously fragile: They “decohere” and lose their quantum properties after frustratingly short intervals of time. “You’d have to prevent it from decohering in your wallet,” Aaronson says.
For many researchers, that makes quantum money even more remote than useful quantum computers. “At present, it’s hard to imagine having practical quantum money before having a large-scale quantum computer,” says Michele Mosca of the Institute for Quantum Computing at the University of Waterloo, in Canada. And these superfast computers must also overcome the decoherence problem before they become feasible.
If engineers ever do succeed in building practical quantum computers—ones that can send information through fiber-optic networks in the form of encoded photons—quantum money might really have its day. On this quantum Internet, financial transactions would not only be secure, they would be so ephemeral that once the photons had been measured, there would be no trace of their existence. In today’s age of digital cash, we have already relieved ourselves of the age-old burden of carrying around heavy metal coins or even wads of banknotes. With quantum money, our pockets and purses might finally be truly empty.
About the Author
Michael Brooks, a British science journalist, holds a Ph.D. in quantum physics from the University of Sussex, which prepared him well to tackle the article “Quantum Cash and the End of Counterfeiting.” He says he found the topic of quantum money “absolutely fascinating,” and adds, “I just hope I get to use some in my lifetime.” He is the author, most recently, of Free Radicals: The Secret Anarchy of Science (Profile Books, 2011).