As wireless communications systems have to accommodate an ever-increasing number of data transfers, a lack of sufficient protocols for ensuring that data is transferred to the correct user could leave systems open to an attack.
Berk Akgun at the University of Arizona and his colleagues explored this type of attack in a recent study in IEEE Transactions on Information Forensics and Security. They found that in some cases, the transfer of data can be degraded by more than 50 percent when massive multiple-input multiple-output (MIMO) is used. Massive MIMO is considered one of the key enabling technologies for 5G networks.
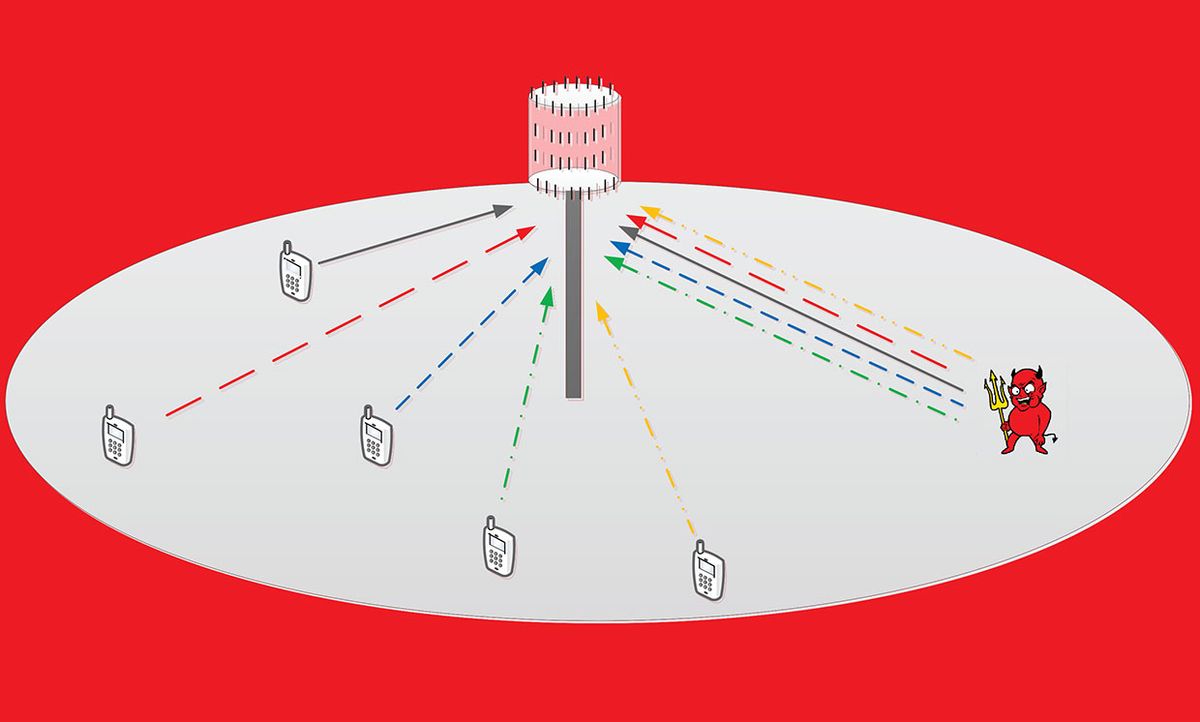
MIMO is a well-established technique in wireless communications whereby two or more transmitters and receivers send and receive data at once. But as base stations transition to massive MIMO, they become equipped with more and more antennas to transmit signals, and these signals are more likely to interfere with one another. To address this issue, smaller, periodic signals called pilots are assigned to and emitted from each user, which ensure that data is transferred to the correct person.
A major constraint of this approach, especially as the number of communication channels for each base station continues to grow, is the limited number of pilots available. Sometimes, users must be assigned the same pilot sequence, which can interfere with the proper transfer of data and lead to poor system performance. This is called pilot contamination. But this contamination can also be harnessed by an attacker to purposely interfere with data transfers.
“An attacker can generate the exact same pilot sequences to those of the legitimate users and transmit these sequences together with these users to distort the channel estimation at the base station,” explains Akgun. This tactic ultimately reduces the data transmission rate to users.
In their study, Akgun and his collaborators explored pilot contamination strategies that an attacker could use under different conditions. Their results show that when an attacker is close to the base station, within 300 meters or closer, he or she can impose their own pilots strongly enough to reduce the total transmission rate of a massive MIMO system by more than 50 percent. Unfortunately, their results also suggest that an attacker can degrade the transmission rates of data from farther distances.
Attacks can also become more severe if the attacker knows the locations of some users. “The attacker has a limited power budget to contaminate the pilot transmissions of legitimate users,” Akgun explains. “If the user locations are known to the attacker, it can distort the pilot transmissions of some users more than it does to others. This way, the adversary can enhance the impact of its attack on the overall system performance.”
Pilot contamination can also be used to siphon off data transfers if the attacker’s pilot signals are strong enough, threatening the privacy of wireless communications. The researchers explored how much this tactic could be maximized under different conditions as well, finding that data transfers are significantly more vulnerable to hacking when the attacker is positioned closer to the base station.
Together, this works underscores the vulnerability of massive MIMO to attack and the need for new protocols for establishing secure communications channels through these systems.
Michelle Hampson is a freelance writer based in Halifax. She frequently contributes to Spectrum's Journal Watch coverage, which highlights newsworthy studies published in IEEE journals.