How Blockchains Work
Illustrated from transaction to reward
Every blockchain needs a way to determine who will add the next block of data. Two strategies prevail: proof of work and proof of stake. Both randomly assign the right to add new blocks. But proof of work gives preference to those with more computing power. And proof of stake—of which there are many versions, some wildly complex—gives preference to those with more coins.
All illustrations: Greg Mably
Miners & Signers
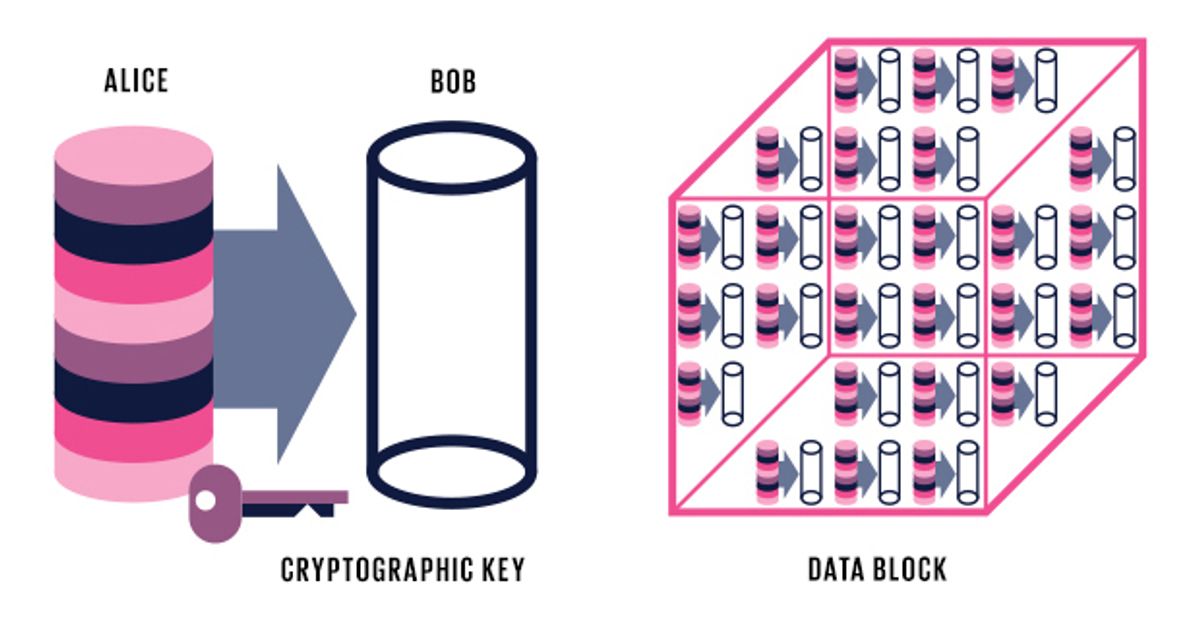
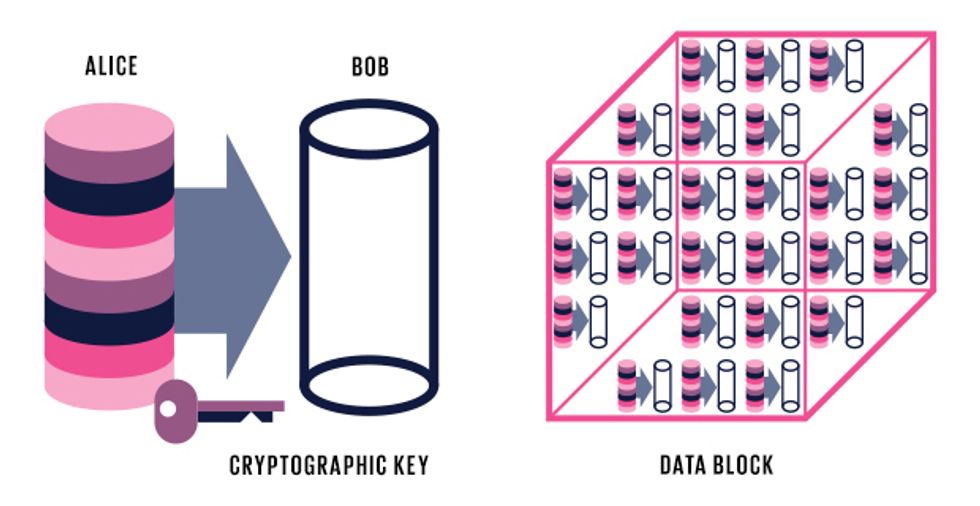
Alice tells the Bitcoin network she wants to pay Bob [left]. She uses a cryptographic key to digitally sign off on the transaction, providing proof that she owns these coins.
Network operators, called miners or block signers, scoop up a bunch of transactions to validate them. They check that the digital signatures are correct and that there are enough coins for the requested transactions. Then they put all the new transactions into a new data block [right] to be added to the blockchain.
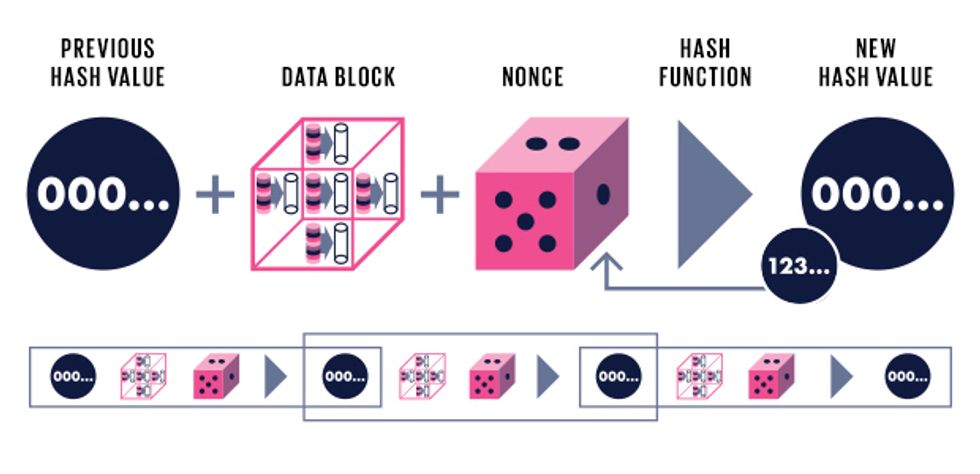
Proof of Work (Bitcoin)
The Bitcoin miner creates a hash from a particular set of data. If the hash does not begin with a particular number of zeros, the hash function is rerun using a new random number (the nonce). Including previous blocks in every new hash compounds the difficulty of tampering with older transactions.
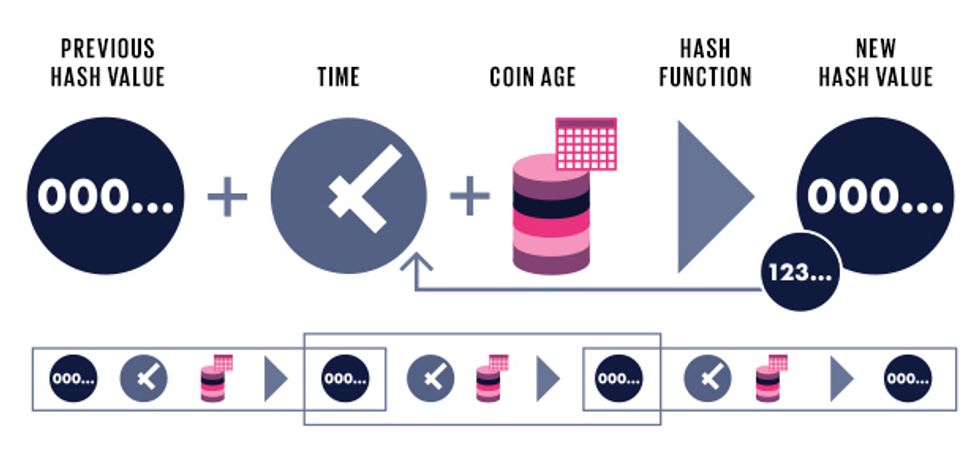
Proof of Stake (Peercoin)
The Peercoin block signer creates a hash from a set of data that includes coin age—a number indicating an amount of coins owned by the signer and how long they’ve owned them. If the hash does not begin with a particular number of zeros, the function is rerun using a new time stamp.
Paying for Security
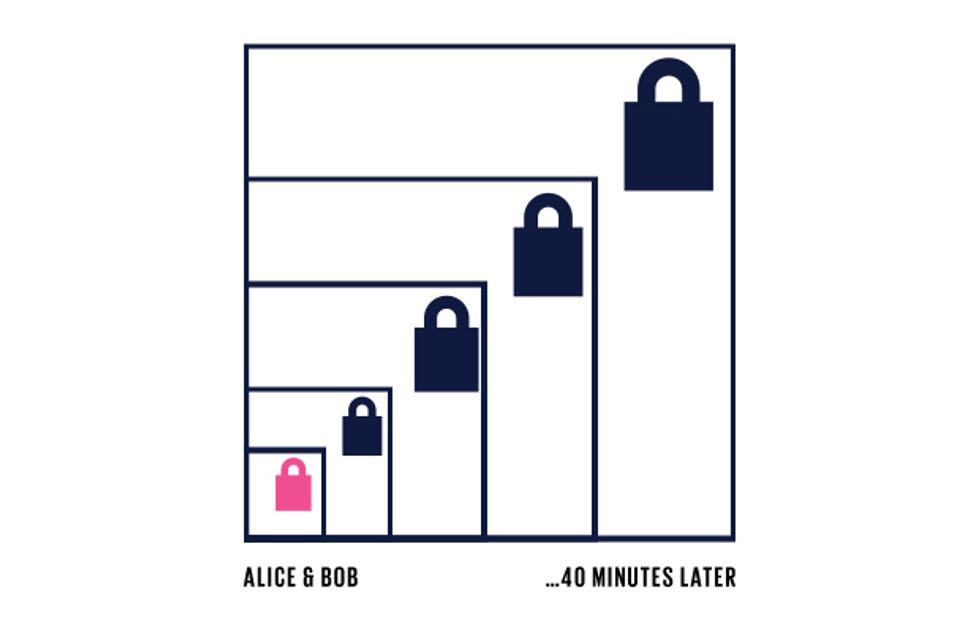
The first miner or block signer to get the right hash adds their version of the block of transactions to the blockchain. They also get paid in newly generated coins.
As more blocks are added, it becomes harder and harder to hack old transactions.
See “Blockchains: How They Work and Why They’ll Change the World.”
 All illustrations: Greg Mably
All illustrations: Greg Mably