A while back I had the idea of taking a cheap MP3 player, a spare infrared sensor, and a bunch of other parts from the back shelf and cobbling them into a motion-activated sound-effects generator. Each time someone walked onto my porch or into the front hall, the gizmo would bombard the intruder with strange noises, perhaps even a series of different voices or animal calls with every approach.
However, as soon as I opened up the player, I knew I was in trouble. The circuit board was about the size of my little finger, the conductors I wanted to solder to were barely visible, there were no posts to wrap a spare wire around and no vias to poke it through. And a few minutes with the manual showed me that even if I managed to connect to the player's controls, I would need something close to artificial intelligence to do anything useful with them. One press of the power button is on, another press of the same button is play, and repeated presses select sound files from a menu pulled up by pressing another button.
The other gadgets I'd planned to cannibalize were pretty much the same--teensy surface-mounted components, complicated controls, questionable outputs. So I put the project aside.
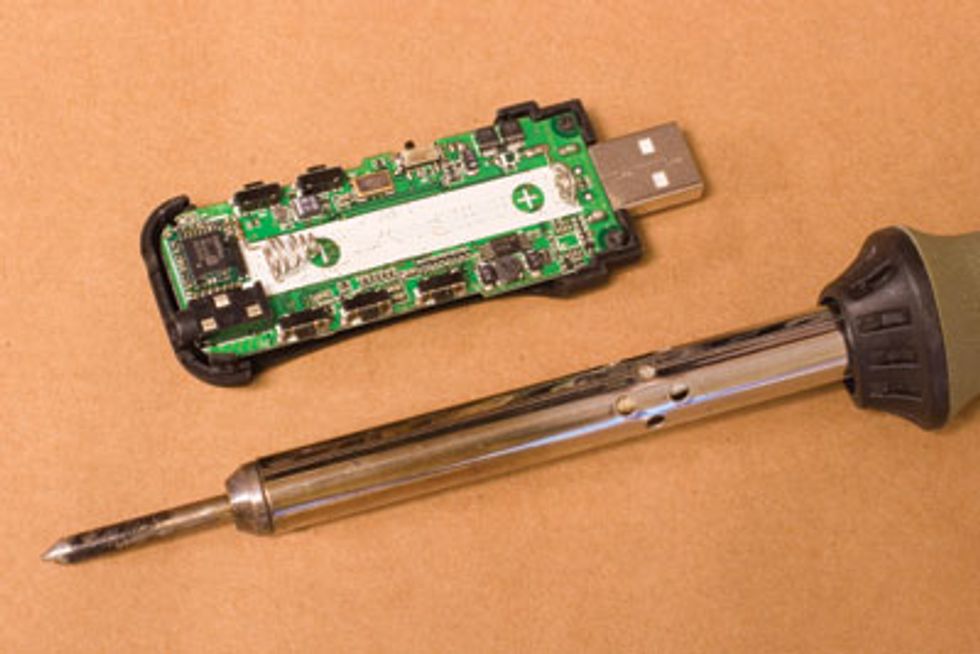
Since then I've been wondering: What's an old-fashioned hardware hacker to do? I've started looking into what it would take to get with the times. Out with the diagonal cutters, in with the tweezers. Out with the soldering iron, in with the miniature hot-air gun and the toaster oven [see photo, "Fat Chance"]. A low-power microscope will come in handy too. And maybe a few microcontroller boards to replace the old on/off switches that used to suffice for controls.
FAT CHANCE: A soldering iron dwarfs today’s circuit elements.
For the hacker with ingenuity, a little cash to spare, and a certain abstract turn of mind, the brave new world of subminiature components and fine-pitch circuits might even be easier to work in than the old one of perfboards (perforated prototyping boards), dead-bug chip packages (whose leads stick up like the legs of a supine insect), and endless jumper wires.
The first thing to go is the soldering iron. For some of the larger-scale surface-mounted components, you can work by tacking down a pin here and a pin there to hold the package in place while you solder the rest. But the point of a typical iron is somewhere between 500 and 1000 micrometers across; the distance between the contacts of a small-outline chip package is closer to 200 µm. Practiced technicians may be able to work with such clearances, but I'm not in that class.
For anywhere from US $250 to well over $1000 you can buy the hot-air guns that full-time engineers and technicians use to rework surface-mount circuit boards, or for about $20 you can build your own. Buy a 45-watt solder sucker from RadioShack, pull off the vacuum bulb, and replace it with heat-resistant plastic tubing connected to an aquarium pump.
Stuff the nozzle with a little copper floss to improve heat transfer. Oh, and don't forget the syringe of solder paste (store it well marked in the refrigerator), because even fine-gauge solder is generally too clumsy for this kind of work.
For the gizmo I wanted to build, I'd also need a microcontroller. For about $40 to $100 I can get a board that I can program to respond to digital or analog inputs with pretty much any sequence of output signals I choose. Hobbyists have a wide selection of microcontrollers, but the Basic Stamp is the canonical, albeit dated, choice of many hackers. Its few dozen bytes of RAM would be enough for me--all I want it to do is turn on the MP3 player, wait a second, trigger the menu-button circuit for a few hundred milliseconds, wait, trigger it again, and so forth.
If I were building something more complicated, the old way would be to mount a bunch of components on perfboard and connect them with jumper wires. There are a few vendors who sell prototyping boards with surface-mount pads that are electrically connected to vias for soldering in jumper wires, but that just doubles the work. For not much more, I could design my own surface-mount board and have it fabricated by a fast-turn service. PCBexpress, for example, offers batches of boards in less than a week for as little as $60.
All the components on such boards can even be soldered in one shot using a domestic toaster oven (preferably not one also used for food). Infrared rays, after all, have the same effect regardless of whether they're produced by a fancy heating element in a factory or a cheap one in the basement. And if you're worried that your fingers can't position components as well as a pick-and-place robot can, it turns out there's a nice self-aligning effect as the surface tension of the molten solder paste pulls pins and pads together.
Will your carefully designed, painstakingly assembled circuit work the first time out of the box? Probably not. Mine seldom do (or not for long). Will your trusty old multimeter tell you anything useful? Probably not. Thank goodness for Moore's Law and technological obsolescence: oscilloscopes of the kind my generation barely dared touch during college lab courses are now available from surplus dealers for not much more than the cost of shipping. They're no good for debugging the latest multigigahertz, multi-CPU nano-mainframe, but they're perfect for watching what goes down a serial line or catching the glitches in my hypothetical button-pressing automaton. And once the malfunction becomes clear, out comes the home-built rework kit to put everything right.
So the next time I have a brainstorm about hacking together some pieces from my junk drawer to make a cool widget, all I have to do is spend a day or two and a few hundred dollars building and buying new tools. I'll need another hundred or so for a microcontroller and a day or two to master its programming idiosyncrasies. Then another few days to learn the software to lay out the printed circuit board. That way I can develop the discipline to think my idea through before I commit it to a circuit design, and the patience to wait until my order comes in. I can hardly wait.
About the Author
PAUL WALLICH is a science writer who lives in Montpelier, Vt.ï»'
To Probe Further
For an overview of hacking printed circuit boards, see https://www.seattlerobotics.org/encoder/200601/article2/index.php.
A good explanation of surface-mount technology is available at https://www.geocities.com/vk3em/smtguide/SMT-GuideV1-3.PDF.
For a tutorial on salvaging parts from old boards, go to https://www.makezine.com/blog/archive/2007/01/how_to_salvage.html.
If you’d like to make your own hot-air gun, visit https://www.engadget.com/2006/03/07/how-to-make-a-surface-mount-soldering-iron.