This hasn’t been a week for major headline-making hacks, but a few interesting stories bubbled to the surface.
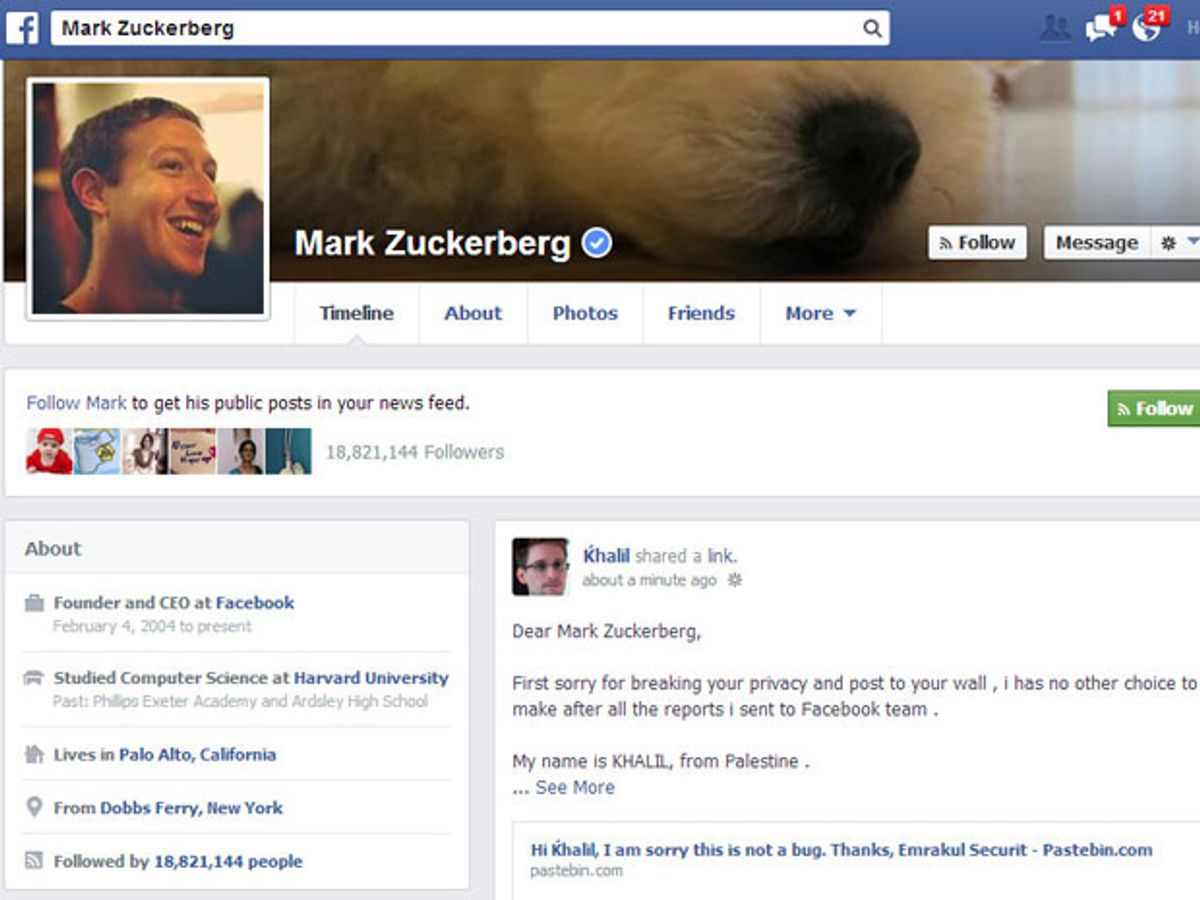
Last week, we reported that a Palestinian security researcher notified Facebook of a security vulnerability on its site by posting a message on the page of Facebook founder Mark Zuckerberg. The struggling researcher, Khalil Shreateh, was looking forward to receiving a reward under the social media site’s bug bounty program for reporting the problem, which would have allowed anyone to post messages to another user’s page, regardless of whether he or she is on the user’s Friends list.
But Facebook denied him, giving itself a PR black eye in the process. It seems Facebook fixed the bug but wouldn’t shell out any money to Shreateh. Why? The site’s security team reasoned that his method of notifying the company—first posting an Enrique Iglesias video to the page belonging to one of Zuckerberg’s college friends, then posting to Zuckerberg's page itself after the security team still insisted that the issue wasn't a bug—violated its terms of service.
Only after Marc Maiffret, CTO of network security firm BeyondTrust, heard about the snub and launched a page whose aim is to raise $10,000 for Shreateh did Facebook try to explain itself.
According to a Wired article, “Matt Jones, a member of Facebook’s security team, posted a note on the Hacker News web site saying a language barrier with Shreateh had been part of the problem for the company’s initial rejection of his submission…He also said that Shreateh had failed to provide any details about the bug that would help Facebook reproduce the problem and fix it.” But the bottom line, despite Jones’ attempts to rationalize a response that came off as miserly, is: 1) Facebook fixed the problem. 2) It was Shreateh who alerted them to it.
“Mistakes were made on both sides,” Jesse Kornblum, a network security engineer for Facebook later told Wired. “We should have asked for more details rather than saying, ‘this is not a bug.’ But Khalil should have demonstrated the vulnerability on a test account, not a real person. We’ve made an interface for [researchers] to create multiple test accounts [for that purpose].”
But Maiffret, who has met his goal (with $3000 coming from his own pocket), says nixing the bounty for the Palestinian researcher sent the wrong message. “It was a good thing that he did,” Maiffret, who got his start as a teenage hacker, told Wired. “He might have done it slightly wrong, but ultimately it was a bug he got killed off before anyone did a bad thing [with it].” Maiffret pointed to his own beginnings, noting that he went from being a rudderless high school dropout to having a successful career after someone agreed to take a chance on him. “Ultimately, [Shreateh] was well-intentioned and hopefully he stays on the same track of doing research,” Maiffret says.
Google App Engine an Unwitting Conduit for Adware
The adware that floods a computer user’s browser with come-ons is nothing new. But purveyors of this pestilence have come up with a new way to spread it. Jason Ding, a research scientist at Barracuda Labs, posted a note on the company’s research blog this week alerting the world that two sites are lacing users’ machines with malware posing as legitimate application software on Google’s App Engine.
According to Ding, the sites, which appeared about a week ago, prey on the inexperienced or inattentive user. The first one (java-update[dot]appspot[dot]com), which passes itself off as a free Java download site, looks a lot like Oracle’s official Java site. But clicking links on this sinister page causes the download of “setup.exe,” which in turn tries to install the Solimba adware program. The endgame for the other site (updateplayer[dot]appspot[dot]com) also involves plaguing the user with Solimba. But instead of baiting users with a Java imposter, it tells them that their media player is outmoded and needs an update. And guess who’s generous enough to offer a just the right fix? Clicking on any of the site’s links pulls down the same executable file that installs Solimba.
The people who set up these sites are using Google’s App Engine as an intermediary because it gives their pitches the air of credibility and hides URLs that would instantly put users on alert that something is fishy.
More People Affected by Outages from Cyberattacks than from Hardware Failures
A report released on Tuesday by the European Union Agency for Network and Information Security (ENISA) reveals some startling information about the reach and effectiveness of cybercrime. Last year, hardware failures accounted for about 38 percent of incidents that resulted in “severe outages of both mobile and fixed telephony and Internet services” in the E.U. These attacks affected 1.4 million people, on average. Though cyberattacks made up 6 percent of European outages last year, each incident affected an average of 1.8 million users.
“League of Legends” Maker Hacked
Marc Merrill and Brandon Beck, founders of video game maker Riot Games, said in a blog post this week that cybercrooks had hacked into its network and gained access to usernames, email addresses, salted password hashes, some first and last names, and encrypted credit card numbers. The company, developer of the online multiplayer game “League of Legends,” says it is looking into just what details were gleaned in the unauthorized access of 120 000 transaction records dating back to 2011.
In Other Cybercrime News…
Reuters: Ex-Soviet hackers play outsized role in cyber crime world
Willie Jones is an associate editor at IEEE Spectrum. In addition to editing and planning daily coverage, he manages several of Spectrum's newsletters and contributes regularly to the monthly Big Picture section that appears in the print edition.