Anonymizing Cellphone Tracking Data Doesn’t Work
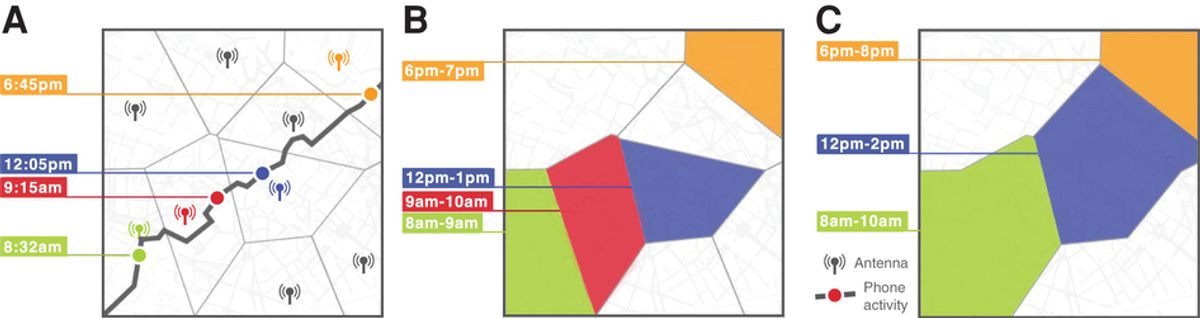
Earlier this month, we highlighted a Data Center of China Internet (DCCI) report revealing that up-to-the-minute information on where people are is becoming a big quarry for cybercriminals. Though that report focused on thieves using malware-laced apps to acquire the location data, researchers from MIT and the Universite Catholique de Louvain in Belgium recently found that anonymized mobile phone location data—the kind that police and other legal authorities might demand from a wireless carrier—can easily be used to home in on the identity of a single cellphone user. The American and Belgian team, which looked at 15 months of anonymized mobile phone data for about 1.5 million European users, found that they could identify 95 percent of them from just four data points. The data points are generated when a handset periodically connects to nearby cell towers as they move and when they make and receive calls and text messages. What’s worse from a privacy standpoint? About half of the users could be identified using only two data points. In a paper published this week in Nature Scientific Reports, the researchers note that:
"We show that the uniqueness of human mobility traces is high, thereby emphasizing the importance of the idiosyncrasy of human movements for individual privacy. Indeed, this uniqueness means that little outside information is needed to re-identify the trace of a targeted individual even in a sparse, large-scale, and coarse mobility dataset. Given the amount of information that can be inferred from mobility data, as well as the potentially large number of simply anonymized mobility datasets available, this is a growing concern."
The concern is warranted because governments including the United States have radically increased their snooping activities. For example, the FBI has gone hog wild issuing so-called National Security Letters (NSLs), which compel businesses such as wireless carriers and Internet service providers to turn over information without a warrant. In 2011, the FBI sent out more than 16 000 NSLs.
The researchers conclude that, “Going forward, the importance of location data will only increase and knowing the bounds of individual's privacy will be crucial in the design of both future policies and information technologies.”
Spam-In-a-Blanket
One way to look at the Internet is as a giant potluck. People from all over the globe are presenting dishes for you to try and it’s up to you to stay away from the ones that are going to cause you harm. And just like at a real-world gathering, there are some people whose cooking you trust because you know them well or their reputations precede them. And others… well, not so much. What some Internet spammers have started doing is akin to stealing one of dear Aunt Sarah’s distinctive ceramic serving dishes and filling it with rancid potato salad of their own making.
Researchers at Barracuda Labs have discovered that some Internet tricksters are getting around reputation filters designed to keep spam out of e-mail inboxes by using Google Translate as its cover. A Kaspersky Lab Threatpost article notes that, “most spam filters will block shady messages if the reputation and destination of any embedded link is shaky. One end-around for this problem is for the spammer to use a mix of open URL redirectors and URL shorteners leading to sites in favor with reputation filters.” And that’s exactly what the Barracuda researchers found. The spammers sent messages containing links shortened using Yahoo’s URL shortening service. The links point, at least initially, to a Google Translate page, which filters will readily accept; that page redirects to a compromised WordPress site that then sends the user to a pharmaceutical website. From there, any type of malware could be pushed onto the user’s system, potentially making it sick.
Cyberthieves Leave Online Sticky Notes to Tell Trojans What to Do
We’ve recently reported on cybercriminals using Skype and Twitter as tools for furthering the spread of malicious code. Now Internet security firm Trend Micro is reporting that a group of hackers has been using Evernote, a cloud-based note-taking and data-sharing service, as a messaging service for data-stealing Trojans. TrendMicro threat response engineer Nikko Tamana told Kaspersky Lab’s Threatpost that the security researchers observed a Trojan connecting to an Evernote and dropping a payload containing a .DLL file that opens a backdoor to a computer. “Upon installation,” says the Threatpost article, “the backdoor has the capacity to download, execute and rename files. It also gathers system information, such as details about its host’s operating system, timezone, user and computer name, registered owner, and organization.” The Trojan gets instructions on what to do with all that information from notes saved on Evernote. This command and control setup is tough to spot and to block because the activity it generates looks just like the legitimate traffic to and from Evernote.
In Other Cybercrime News...
Agents and analysts from the UK’s MI5 and GCHQ will work side-by-side with private sector counterparts in a new government "fusion cell".
A global credit card fraud network was shut down on Thursday as the result of an international police operation called "Pandora-Storm."
Illustration: Yves-Alexandre de Montjoye
Willie Jones is an associate editor at IEEE Spectrum. In addition to editing and planning daily coverage, he manages several of Spectrum's newsletters and contributes regularly to the monthly Big Picture section that appears in the print edition.