Englishman Frederick W. Lanchester (1868-1946) was a major contributor to the foundation of automotive and aeronautical engineering. He also published works on radio, acoustics, warfare, and even relativity. His equations of combat form the basis of the science of operations research. (These equations have been used to formulate business strategy in recent times.) He was the first to describe the aeronautics of lift and drag. His automobile inventions include the gas engine starter, rack-and-pinion steering, disk brakes, four-wheel drive, and fuel injection.
In his historic 1916 paper "Mathematics in Warfare," Lanchester presents two simple differential equations relating force attrition to the number of forces or weapons in opposition and to their effectiveness (see sidebar "Lanchester's Equations"). The equations' solutions show that the effectiveness of a force is directly proportional to the effectiveness of its weapons and to the square of its numbers. The following table illustrates how Lanchester's equations would apply in a classic artillery duel:
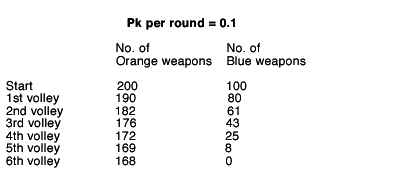
The Lanchester Exchange: Artillery Duel
The table shows 200 weapons arrayed against 100 weapons with equal kill probabilities (Pk) of 10 percent. In the first round, Orange kills 20 Blues, and Blue kills 10 Oranges--leaving 190 Oranges to kill 19 of the remaining 80 Blues, while the Blues kill 8 Oranges in the second round. At the end of the sixth round, all the Blues are gone and 168 Oranges (84 percent) remain.
Note that each side engages only the remaining live targets. If neither side can tell when it has killed a target, as in some artillery duels, both sides must continue to shoot at all the targets, thereby wasting part of their efforts. Lanchester analyzed this problem also and showed that the impact of numbers is a linear not square law.
Bob Everett, former president of The MITRE Corp., noted that that was reasonable, because in the square-law example, "you get one power from the number of weapons shooting at the other side and the other power from the reduced number of targets you have to shoot at."
The advantage of telling dead from live targets is one of the reasons that artillery forces use spotters and counter-battery radar and that air forces use bomb-damage assessment after air attacks.
(Please see, " " for a graphic representation of the difference in attrition.)
Of course, wars aren't fought in accordance with mathematical equations, and there are many other important factors, including leadership, discipline, morale, training, and health. Nevertheless, analysis of battles between conventional forces over the years has supported the thrust of Lanchester's Law: numbers do make a huge difference.
In the 1985 book Race to the Swift, British military analyst Richard E. Simpkin notes that "for a conflict between two large, sophisticated mechanized forces, one did not go far wrong with a '1.5 law'--a halfway house between Lanchester's two cases."
Lanchester's paper appears in Volume 4 of mathematician James Newman's delightful The World of Mathematics collection. (Incidentally, to give you some feeling of what Newman thinks of our profession, he writes in his commentary on Lanchester, "His writings on these matters, apart from high professional competence, exhibit such striking independence of judgment and boldness of conception that it is surprising to learn he was an engineer." Oh, well.)
Lanchester and the Cold War
During the Cold War, in the strategic nuclear area, the United States wisely opted for parity in numbers and, generally, some superiority in weapons capability. However, in the tactical arena, the United States took a different approach. The Warsaw Pact nations had overwhelming numerical superiority in almost all categories of conventional forces--infantry, tanks, artillery, tactical aircraft, and so on--ranging from 2:1 to 5:1. NATO based its counter to such numbers on a substantial conventional force plus tactical nuclear weapons. The plan called for 15 000 nuclear weapons: artillery shells, warheads for surface-to-surface and surface-to-air missiles (SSMs and SAMs), and nuclear bombs for tactical aircraft. Although most of the weapons were fabricated--deployment to Europe was limited to about 7000--the threat of their use effectively countered any Warsaw Pact offensive capability for more than two decades.
However, over time, similar advances by the Soviets overtook that "solution," and there were concerns about crossing the nuclear threshold and triggering strategic exchanges. Therefore, NATO began considering a conventional solution to the numerical disparity.
In the mid-1970s, as the United States started to rebound from the Vietnam War, key analyses by BDM International (a defense consulting and research firm) and Martin Marietta prompted the U.S. Department of Defense to readdress the conventional-force imbalance. One effort was a Defense Science Board (DSB) study in 1976 titled "Conventional Counters to a Pact Attack." The charge was to see what technology could do to help counter the numerical discrepancy.
Early in the study, one of the board members, MITRE's Ed Key, pointed out the relevance of Lanchester's Law, and it became a major theme of the study. The first conclusion of the DSB study noted the importance of a surveillance system that could provide NATO forces an accurate and timely picture of enemy force distribution with an appropriate command, control, and communications (C3) structure, which together would allow commanders to achieve, in some cases, local numerical superiority and, in others, to avoid local numerical inferiority.
A second thrust was to seek systems for asymmetrical engagements whose effectiveness would be sufficiently great to overcome numerical square-law advantages. Because, for example, it would be nearly impossible to make NATO tanks nine times as good as Warsaw Pact tanks to overcome the 3:1 numerical advantage, other means of effectively attacking tanks, whereby the tank had essentially zero capability against the attacker, were sought. Several promising approaches were identified and many more were conceived by the Defense Department and vigorously pursued.
The thrust of asymmetrical engagements is to avoid force against a numerically superior similar force until the enemy force has been substantially weakened. The combination of those capabilities led to the term "force multiplier," which rapidly became a buzzword in the military community.
The third finding of the DSB study was: if good surveillance and C3 were good for NATO, then countering or disrupting Warsaw Pact surveillance and C3 would be bad for the enemy. The Defense Department launched a substantial C3 countermeasures (C3CM) effort, and the term "force divider" was born. C3CM is yet another form of asymmetric engagement.
By the late 1970s, Defense Department speeches were awash with Lanchester. To rephrase an old maxim: You couldn't throw an empty beer bottle through a window without hitting some major giving a talk on Lanchester's equations.
Lanchester and the Gulf War
Meanwhile, throughout the last half of the 1970s and through the 1980s, Bill Perry, then Defense Department undersecretary for research and engineering, and his successors concentrated on developing a set of capabilities that would reduce the Warsaw Pact's numerical advantages. Developments included better platforms (such as the M-1 tank), systems for vastly reducing the effectiveness of some enemy systems (such as stealth aircraft and C3CM approaches), and systems for greatly improved surveillance, C3, and asymmetric engagements.
Although, happily, war with the Warsaw Pact alliance was avoided, the success and broad applicability of U.S. efforts were demonstrated by the rapidity and completeness of the 1991 Persian Gulf War victory.
Here are two interesting examples:
1. Opening attacks by Tomahawk cruise missiles and stealth aircraft crippled the Iraqi C3 system. Those attacks were followed by air-launched anti-radiation missiles to finish off the high-altitude SAMs, which allowed U.S. tactical aircraft to operate with relative impunity above the coverage of short-range infrared missiles and "plink" enemy tanks and artillery with laser-guided bombs.
2. Before completing its encirclement, the famous deceptive "left hook" was apparently discovered, and an Iraqi force attempted to move into a blocking position. This movement was detected by the JointSTARS aircraft, which uses a special radar to detect and track moving ground vehicles.
In discussing the lopsided outcome of the Gulf War, Perry compared it to a basketball game that ended 100-1. Could the winning team have shot that much better or rebounded, defended, and passed that much better? No, the team that lost was blindfolded, and the team that won had perfect vision.
The war's Desert Storm operation was unquestionably one of the most studied of all time. Many groups and nations analyzed it. India, for example, produced a five-volume report.
The principal conclusion was that U.S. capabilities in conventional tactical wars were so great and represented such a sizable investment that no sensible nation would challenge the United States in a direct conventional war, provided it retained such capabilities. Suggested countermeasures were generally in two categories: high tech and low tech.
High Tech: Nearly all studies noted that the overwhelming U.S. capabilities depended on large air bases and logistic supply centers near the war zone. The high-tech counter would be to make such facilities dangerous to use. Such a counter would provide, much as the newer U.S. capabilities have, huge leverage and represent a significant asymmetric engagement capability.
Low Tech: It was also noted that, whereas in past battles between conventional forces the relative size and capabilities of the forces played a dominant role, there have been many cases where one side with grossly inadequate conventional forces, or none at all, adopted tactics that offset conventional capabilities. The difficulties the U.S. military had in the Vietnam War were especially noted and, thus, the low-tech counters suggested were forms of guerrilla warfare, including urban and jungle operations. Such low-tech counters largely avoid traditional battles and, therefore, thwart the effectiveness of most modern military capabilities. In addition, without conventional engagements, neither Lanchester nor its counters apply.
In the 1990s, the United States continued developing advanced asymmetric engagement capabilities, including greatly improved surveillance, situation awareness, and Global Positioning System (GPS)-guided weapons. Meanwhile, several nations, drawing on the lessons learned from Desert Storm, pursued the high-tech counter. Iran, North Korea, Syria, India, and Pakistan developed longer range, more accurate ballistic missiles that would allow them to put any nearby bases at risk and, thus, attenuate or deny U.S. capabilities.
For example, the Iranian Shahab-3 intermediate-range ballistic missile (IRBM), with a 1-ton warhead and a range of 1200 miles, can cover the entire Arabian Peninsula and more. Such a weapon, even with a conventional warhead, could create serious problems for the United States. With a WMD warhead, the situation probably would be untenable. The Shahab-3 is a derivative of the North Korean Nodong missile. Clearly, the deterrent value of IRBMs is greatly increased if they have nuclear warheads--which probably accounts for the priority efforts by Iran and North Korea to develop such missiles.
The military value of the further enhanced U.S. capabilities was demonstrated during the rapid defeat in 2002 and 2003 of Afghan and Iraqi forces using conventional combat.
After rapidly defeating the Iraqi military and toppling its dictator, the United States set about rebuilding the country and creating a democratic form of government. However, the U.S.-organized coalition has faced a serious insurgency problem in Iraq (and, to some extent, in Afghanistan). By adopting the low-tech lessons learned from the first Iraq war, the insurgents have resorted to an extreme form of asymmetry, the tactics of terrorism.
(Note: The use of terrorism by Islamic extremists is now frequently referred to as "asymmetric warfare.")
Lanchester and the Iraq War
The United States finds itself, once again, in a situation where its superb military capabilities are largely ineffective. The U.S. military is, in a sense, now on the other side of the Lanchester equation. As in Vietnam, it has great numerical superiority over its enemy but has yet to find effective ways to deal with low-tech counters.
Lanchester's Law deals with the forces engaged. By choosing the time, place, and type of action, the insurgents can achieve a huge asymmetric advantage and even, in some cases, local numerical superiority. An improvised explosive device (IED) can be covertly planted by a few people and later remotely detonated by a single, hidden individual. The insurgents can organize an attack or ambush on a small number of our troops where they have numerical advantage.
At this point, we've stretched Lanchester well beyond its applicability. A colleague has noted that Lanchester applies to armies fighting according to Marquis of Queensberry rules, something guerrillas and terrorists don't do.
The problem for the conventional force is finding and identifying someone to fight. The only way greater numbers help is that more troops can search more areas and monitor more streets, buildings, and borders. The problem is made even more difficult because the insurgents are not necessarily trying to win a battle. (After all, in Vietnam, U.S. forces decisively won nearly all the military battles.)
There's an old saying, "To a man with a hammer, everything looks like a nail." History suggests this additional version: "To the leaders of a nation with an overwhelmingly powerful military, every problem looks like it has a military solution."
Clearly, though, current U.S. military capabilities, overwhelming as they are, have not allowed the United States to squelch the insurgency.
Here's another "hammer-nail" observation: "To a nation with a superb technology base, every problem, including military ones, looks like it has a technology solution." The United States, as it has frequently done, has turned to technology to provide solutions. The record is mixed.
Technology and Asymmetry
World War II was the first time the United States organized the national scientific community to aid in the war effort. President Franklin D. Roosevelt approved establishment of the National Defense Research Committee and the Office of Scientific Research and Development (OSRD). Directed by Vannevar Bush of the Massachusetts Institute of Technology, the OSRD created scientific centers to address major military issues. Each had civilian leadership and near total freedom from federal government interference. The largest were the MIT Radiation Lab, which developed nearly all the U.S. microwave radars; the Harvard Radio Research Lab, which developed intercept and jamming systems; and the Manhattan Project, which developed the atomic bomb.
Each of those organizations had a close, constructive working relationship with the uniformed military, and the use of technology to address military problems worked magnificently. After World War II, a strong coupling continued between the Defense Department and the scientific community at the Los Alamos, Sandia, and Lawrence Livermore labs. With strong emphasis on the strategic area, including continental air defense, conventional forces had about zero technical attention until the Vietnam War.
During the Vietnam War, in spite of overwhelming superiority in conventional military capability, the United States was unable to figure out how to deal with the enemy's guerrilla warfare other than using nuclear weapons or invading North Vietnam. (In retrospect, it seems clear that neither approach would have achieved a favorable long-term outcome for the United States.)
The U.S. military fielded many new systems in Vietnam, including "people sniffers," quiet airplanes, portable combat surveillance radars, infrared imaging detectors, and a system designed to interdict the flow of supplies down the Ho Chi Min Trail from North Vietnam to the Viet Cong in the south, the so-called McNamara Line. (The McNamara Line is worth further comment, because the approach, as implemented, made the common error of ignoring "feedback"--that is the reaction of those affected to changed circumstances.)
The basic idea for the interdiction system came from JASON, a group of largely academic scientists who address various difficult Defense Department problems--usually during a lengthy summer study. The system consisted of many acoustic and seismic sensing devices planted along the trail to detect people and vehicles; a comprehensive communications network tying everything together; and a large, computer-based control station in Thailand to analyze the sensor inputs and to control air strikes against the movers.
After the United States created and deployed the large, creative system and devoted thousands of air sorties as part of the operation, sufficient supplies continued to flow to the Viet Cong. In spite of its massive technology effort, the United States continued to suffer casualties and made little, if any, progress in winning the war. (It should be noted, though, that those technology efforts resulted in a number of significant additions to U.S. conventional capabilities, such as infrared detectors for night operations, laser-guided bombs, unattended ground sensors, and gunships.)
One can't help but be struck by the disturbing similarity to the U.S. drug interdiction program, where in spite of massive expenditures of resources, the street price has remained relatively constant.
Lanchester and Low Technology
In the case of the Ho Chi Min Trail supply system, the enemy mustered enough redundancy and slack to meet demand in spite of the Americans' best efforts to counter it.
Both the Ho Chi Min Trail and the illegal drug supply system designs include enough redundancy and slack to meet demand in spite of the best efforts to counter them. Moreover, neither technology nor major military or similar efforts have provided a satisfactory solution to the problem. In many ways, dealing with insurgents in Iraq is similar. There are many different situations, circumstances, and times where terrorism can be employed. The place, time, and type of action are decided by the insurgents, who are not trying to win battles, just the "war," and their timescale is very long.
When IEDs and suicide bombers began showing up, the United States brought its vast technological and intelligence resources to bear. There is a major effort by industry, not-for-profits, government labs, and the entire intelligence apparatus to counter the threats and to track down the insurgents and their leaders.
Many clever devices, techniques, and systems have been developed and fielded, and a number of isolated successes have been achieved. Although the efforts have helped and other devices and systems are likely to be deployed and to help, the United States remains a long way from solving the problem. As with the Viet Cong, the insurgents have an almost endless variety of options.
It turns out that having a great technological capability and relying on it may be a disadvantage. I recently ran across T.E. Lawrence's Principles of Insurgency. Each is pungent and seemingly applicable to Iraq, especially the second and fourth ones:
1. A successful guerrilla movement must have an unassailable base.
2. The guerrilla must have a technologically sophisticated enemy.
3. The enemy must be sufficiently weak in numbers so as to be unable to occupy the disputed territory in depth with a system of interlocking fortified posts.
4. The guerrilla must have at least the passive support of the populace, if not its full involvement.
5. The irregular force must have the fundamental qualities of speed, endurance, presence, and logistical independence.
6. The irregular must be sufficiently advanced in weaponry to strike at the enemy's logistics and signals vulnerabilities.
On reading the rules, one can't help but wish someone in authority had studied them prior to the invasion decision.
Summary
Let's recap. Starting in the mid-1970s, the United States turned its attention to countering the Warsaw Pact's substantial numerical superiority in conventional weapons, principally through the use of advanced technology. The U.S. effort, which continued throughout the 1990s, resulted in the creation of many important military capabilities.
By the end of the century, those capabilities--supplemented by an emphasis on excellent training facilities and programs involving many exercises--produced the most capable military force ever assembled. It was a force that rapidly defeated a major Iraqi force and a scattered Taliban force with minimal U.S. losses. However, it is designed to fight against other military forces; it is neither designed for nor capable of countering a determined insurgency.
Overall, one ruefully concludes that it is unlikely there is a military or a military-technical solution to the low-tech asymmetric warfare in Iraq.
That is not to say that technology won't play a part in homeland defense. It will and should play an important role.
And then there is the broader issue of worldwide Islamic violence, which some have also called asymmetric warfare or, as a British analyst said after the London subway tragedies, a "revolution in the nature of conflict." Here, also, it would seem that the eventual solutions will lie outside the military and military-technical realms.
About the Author
IEEE Fellow Charles A. "Bert" Fowler of C.A. Fowler Associates has been a consultant to industry and government since 1986. His major field is electronics, with specialties in radar; command, control, and communications (C3); counter-C3; intelligence; and military systems. He has held a wide range of industrial positions, most recently as senior vice president of MITRE Corp. He was a member of the Defense Science Board (Chair 1984-1988) and the Defense Intelligence Agency, Science and Technology Advisory Board (Chair 1976-1982); and is a member of the National Academy of Engineering.